Your organization has invested millions in cybersecurity infrastructure. Firewalls, endpoint protection, SIEM, SOAR, identity controls, cloud security. On paper, you should be well protected. In reality, most organizations have no continuous way to verify whether those defenses actually work when attackers try to break in.
This is not fear mongering. By 2026 a majority of security leaders openly acknowledge they feel underprepared for a serious cyber attack, despite record spending. Traditional security testing still happens episodically, often once or twice a year, leaving long blind spots where new misconfigurations, software changes, and emerging attack techniques go completely untested. Many teams only discover defensive gaps after an incident forces the issue.
At the same time attackers are moving faster and more systematically. Automated tooling allows them to probe defenses continuously, chaining weaknesses across email, identity, endpoints, cloud workloads, and data paths. Relying on static controls without validation is no longer a defensible strategy.
This is where Breach and Attack Simulation tools fundamentally change the model. Instead of assuming controls work, BAS platforms continuously simulate real-world attacks against your environment, validating detection, prevention, and response in real time. Unlike traditional penetration testing that delivers a snapshot, BAS provides ongoing evidence of security effectiveness as threats evolve.
With breach costs remaining in the multi-million dollar range and attacks accelerating in frequency and sophistication, hoping your defenses work is not a strategy. Proving they work is.
Quick Comparison Overview
| Tool | Best For | Deployment Speed | Starting Price Range |
|---|---|---|---|
| Cymulate | Continuous security validation across multiple attack vectors | Quick (Days) | $7,000/month |
| SafeBreach | Automated attack simulation with extensive playbooks | Moderate (1-2 weeks) | $50,000+/year |
| AttackIQ | Security control validation and purple team exercises | Quick (Days) | $40,000+/year |
| Picus Security | Measuring and improving security control effectiveness | Quick (Days) | $30,000+/year |
| Mandiant Security Validation | Enterprise-grade validation with threat intelligence | Moderate (2-4 weeks) | $100,000+/year |
| Pentera | Automated penetration testing and attack path analysis | Moderate (1-2 weeks) | $75,000+/year |
| NodeZero | Autonomous penetration testing and validation | Quick (Days) | $25,000+/year |
1. Cymulate — Market Leader in Continuous Security Validation
Best for: Organizations needing comprehensive, continuous security posture assessment
Cymulate leads the Continuous Threat Exposure Management (CTEM) market, offering a platform that validates exposures, prioritizes risk, and drives continuous threat exposure management. As of 2025, Cymulate holds a 20.7% market share in the BAS category, making it the top choice for organizations seeking comprehensive security validation.
Key Strengths:
- Multi-vector simulation: Tests email security, web application security, endpoint security, network security, and data exfiltration
- Immediate deployment: Cloud-based platform with rapid setup
- Executive reporting: Clear dashboards that translate technical findings into business risk
- Integration capabilities: Works seamlessly with existing security tools and SIEM platforms
Pricing: Starting around $7,000/month for up to 1,000 endpoints with 7 attack vector bundle
Limitations: Interface complexity can require training for full utilization. Premium pricing may be challenging for smaller organizations.
2. SafeBreach — Pioneer in Automated Attack Simulation
Best for: Security teams wanting automated, continuous attack simulation
SafeBreach pioneered breach and attack simulation, running continuous, real-world attack scenarios powered by its extensive Hacker's Playbook™—a constantly updated collection of attack techniques. The platform excels at uncovering hidden vulnerabilities through automated testing scenarios.
Key Strengths:
- Hacker's Playbook™: Extensive library of attack methods updated continuously
- Automated remediation guidance: Provides specific steps to fix identified issues
- Multi-platform coverage: Tests Windows, Linux, macOS, and cloud environments
- Attack path visualization: Shows how attackers could move through your network
Pricing: Typically starts around $50,000+ annually for enterprise deployments
Limitations: Market share declined from 9.7% to 6.2% in 2025, indicating potential competitive pressure. Setup complexity may require dedicated resources.
3. AttackIQ — Security Control Validation Specialist
Best for: Organizations focused on validating specific security controls and supporting purple team exercises
AttackIQ's standout Anatomic Engine can test ML and AI-based cybersecurity components, running multi-stage emulations, testing network controls, and analyzing breach responses. AttackIQ maintains a strong 4.8-star rating with 84 verified reviews.
Key Strengths:
- MITRE ATT&CK alignment: Tests mapped to specific attack techniques and tactics
- Purple team support: Facilitates collaboration between red and blue teams
- Flexible deployment: Available as SaaS, on-premises, or hybrid
- Detailed analytics: Comprehensive reporting on security control effectiveness
Pricing: Enterprise licensing typically starts around $40,000+ annually
Limitations: Room for improvement in integration capabilities with other platforms, which may limit versatility in complex environments.
4. Picus Security — Threat-Informed Defense Validation

Best for: Organizations wanting to measure and continuously improve security control effectiveness
Picus Security received high rankings among BAS solutions in 2025, focusing on threat-informed security validation. The platform emphasizes practical, actionable insights over theoretical assessments.
Key Strengths:
- Threat-informed approach: Simulations based on current threat intelligence
- Mitigation guidance: Specific recommendations for improving security posture
- Easy deployment: Quick setup with minimal infrastructure requirements
- Cost-effective: Competitive pricing for mid-market organizations
Pricing: Generally more accessible than enterprise-focused competitors, starting around $30,000+ annually
Limitations: May lack some advanced features found in higher-end platforms. Smaller vendor with potentially limited support resources.
5. Mandiant Security Validation — Enterprise Threat Intelligence Leader
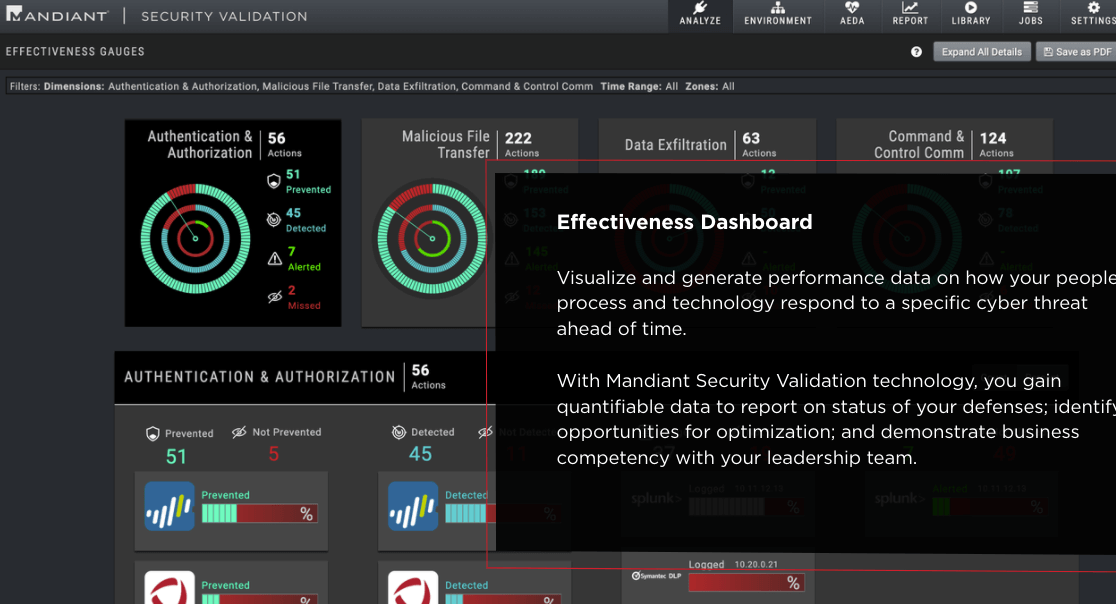
Best for: Large enterprises requiring threat intelligence-backed security validation
Verodin was acquired by FireEye in 2019 and integrated into the Mandiant Security Validation platform, with Mandiant now part of Google. This platform combines security validation with world-class threat intelligence capabilities.
Key Strengths:
- Threat intelligence integration: Simulations based on real-world threat actor behaviors
- Enterprise scalability: Designed for large, complex environments
- Google backing: Strong financial support and development resources
- Expert services: Access to Mandiant's incident response expertise
Pricing: Premium pricing typically starting around $100,000+ annually for enterprise deployments
Limitations: High cost may be prohibitive for smaller organizations. Complex implementation requiring significant planning and resources.
6. Pentera — Automated Penetration Testing Platform
Best for: Organizations wanting automated penetration testing combined with attack simulation
Pentera ranks as a top BAS solution for 2025, offering automated penetration testing that goes beyond simulation to actual safe exploitation of vulnerabilities.
Key Strengths:
- Safe exploitation: Actually exploits vulnerabilities without causing damage
- Network mapping: Comprehensive discovery and analysis of attack paths
- Automated reporting: Detailed findings with clear remediation priorities
- Compliance support: Helps meet regulatory requirements for security testing
Pricing: Mid-to-high range pricing, typically $75,000+ annually
Limitations: More complex than pure simulation tools. Requires careful scoping to avoid disrupting production systems.
7. NodeZero — Autonomous Security Validation
Best for: Organizations seeking autonomous, AI-driven security validation with minimal oversight
NodeZero Platform ranks among the top 5 BAS solutions, offering autonomous penetration testing that requires minimal human intervention.
Key Strengths:
- Autonomous operation: AI-driven testing requiring minimal human oversight
- Safe and reliable: Designed to test without disrupting business operations
- Comprehensive coverage: Tests multiple attack vectors automatically
- Clear reporting: Executive and technical reports for different audiences
Pricing: Competitive pricing starting around $25,000+ annually
Limitations: Newer platform with potentially less market validation. Autonomous nature may provide less customization than manually configured tools.
How to Choose the Right BAS Tool: Decision Framework
| Evaluation Criteria | Why It Matters | What to Look For | Recommended Tools |
|---|---|---|---|
| Continuous vs. Point-in-Time Testing | Threats evolve constantly; your validation should too | 24/7 automated testing capabilities | Cymulate, SafeBreach |
| Attack Vector Coverage | Different tools excel at different attack types | Email, web app, network, endpoint, and data exfiltration testing | Cymulate, AttackIQ |
| Integration Requirements | Tool must work with your existing security stack | SIEM, SOAR, and security tool integrations | AttackIQ, Mandiant |
| Deployment Complexity | Faster deployment means quicker time to value | Cloud-based platforms with rapid setup | Picus Security, NodeZero |
Budget Planning Guidelines
Small to Mid-Market ($25K-50K budget):
- NodeZero or Picus Security for cost-effective validation
- Focus on automated testing with clear reporting
Enterprise ($50K-100K budget):
- Cymulate or AttackIQ for comprehensive coverage
- Include professional services for optimal configuration
Large Enterprise ($100K+ budget):
- Mandiant or Pentera for advanced capabilities
- Consider hybrid approaches combining multiple tools
Pro Tips for BAS Implementation Success
Start with a pilot program: Begin with one business unit or network segment to prove value before organization-wide deployment.
Define clear success metrics: Establish baselines for mean time to detection (MTTD) and mean time to response (MTTR) before implementing BAS tools.
Plan for integration: Ensure your chosen BAS tool can feed findings into existing workflows, ticketing systems, and security orchestration platforms.
Train your team: Even the best BAS tool requires skilled operators who understand how to interpret findings and translate them into actionable security improvements.
Final Recommendations
By 2026 Breach and Attack Simulation has moved from a niche security function to a core pillar of modern cyber defense. The organizations seeing the most value from BAS are not using it as a compliance checkbox, but as a continuous feedback loop between security controls, detection teams, and leadership.
Cymulate stands out for organizations that want broad, continuous validation across multiple attack vectors with strong executive reporting. AttackIQ is best suited for teams focused on control-level validation and purple team workflows aligned to specific adversary techniques. SafeBreach remains effective for automated attack simulation using extensive playbooks, while Pentera and NodeZero appeal to teams that want more autonomous testing with clear attack path visibility. Mandiant’s platform fits large enterprises that want validation grounded in real-world threat intelligence and expert services.
The most important decision is not which vendor you choose, but how you operationalize BAS. Start small with a pilot, define success metrics tied to detection and response improvement, integrate findings into remediation workflows, and review results regularly with both technical and executive stakeholders.
Security controls that are not continuously tested will fail silently. BAS tools ensure failures are discovered on your terms, not an attacker’s. In a threat landscape defined by speed and automation, validation is no longer optional. It is the difference between believing you are secure and knowing it.


