Cyber attacks are happening roughly every 39 seconds, and most organizations still do not realize they have already been compromised. In 2026 the average enterprise breach remains undetected for many months, giving attackers time to move laterally, escalate privileges, and quietly exfiltrate data. Traditional signature-based security tools are failing against this threat landscape. They react only after damage has begun and flood security teams with alerts that lack context, confidence, or clear next steps.
The painful reality is that many organizations still discover breaches close to nine months after initial compromise. By that point customer data has been exposed, operations disrupted, regulatory risk escalated, and reputational damage locked in. The old strategy of building higher walls around the perimeter no longer works when modern attackers assume they will get inside and design attacks to blend in.
This is where AI-powered threat detection fundamentally changes the equation. Instead of relying on known attack signatures, these platforms learn what normal behavior looks like across users, devices, and networks. They identify subtle anomalies in real time, investigate them automatically, and in many cases respond without waiting for human intervention. In 2026 AI-driven detection is no longer experimental. It is becoming the baseline for organizations that want to reduce dwell time and regain control over their security posture.
This guide cuts through the marketing noise to explain how leading AI threat detection platforms actually perform in real environments, and how to choose the right one before an incident forces the decision for you.
Quick Comparison Overview
| Tool | Primary Strength | Deployment Complexity | Best Use Case |
|---|---|---|---|
| Darktrace | Autonomous response & self-learning AI | Moderate | Enterprise networks needing 24/7 autonomous protection |
| Vectra AI | Network traffic analysis & behavioral detection | Moderate | Organizations with complex network infrastructures |
| Cynet | All-in-one security operations | Low-Medium | Mid-market companies wanting consolidated security |
| CrowdStrike Falcon | Cloud-native endpoint protection | Low | Organizations prioritizing endpoint security |
Darktrace — The Self-Learning Immune System

Best for: Enterprises requiring autonomous threat response
Darktrace pioneered the concept of "AI immune system" for cybersecurity. The platform uses unsupervised machine learning to understand normal network behavior and automatically responds to threats without human intervention.
Key Capabilities:
- Autonomous Response: Neutralizes threats in seconds, not hours
- Enterprise Immune System: Models normal behavior for every user and device
- Zero-Day Detection: Catches unknown attacks other tools miss
- Cross-Platform Coverage: Email, network, cloud, endpoint, and industrial systems
Real-World Impact: A major bank prevented a $45M wire fraud attempt when Darktrace detected unusual credential usage patterns within minutes—something traditional tools completely missed.
Deployment: 24-48 hours for basic deployment; 2-4 weeks for full optimization across complex environments.
Limitations: High cost; requires executive buy-in; learning period of 30-60 days for optimal performance.
Vectra AI — Network Behavior Analytics Leader

Best for: IT security teams focused on network threat hunting
Vectra AI specializes in detecting cyberattacks through network traffic analysis and behavioral modeling. The platform excels at identifying attackers who have already bypassed perimeter defenses.
Key Capabilities:
- Attack Behavior Detection: Identifies attack progressions across the kill chain
- Network Traffic Analysis: Deep packet inspection with AI correlation
- Threat Prioritization: Reduces alert fatigue by focusing on real threats
- Cloud & On-Premises: Unified visibility across hybrid environments
Real-World Impact: A healthcare system discovered a 6-month-old breach when Vectra identified lateral movement patterns in their network—the attacker had been quietly exfiltrating patient records.
Deployment: 1-3 days for initial setup; 1-2 weeks for full tuning and integration.
Limitations: Requires network expertise; primarily focuses on network layer (less endpoint coverage).
Cynet — 360-Degree Security Operations
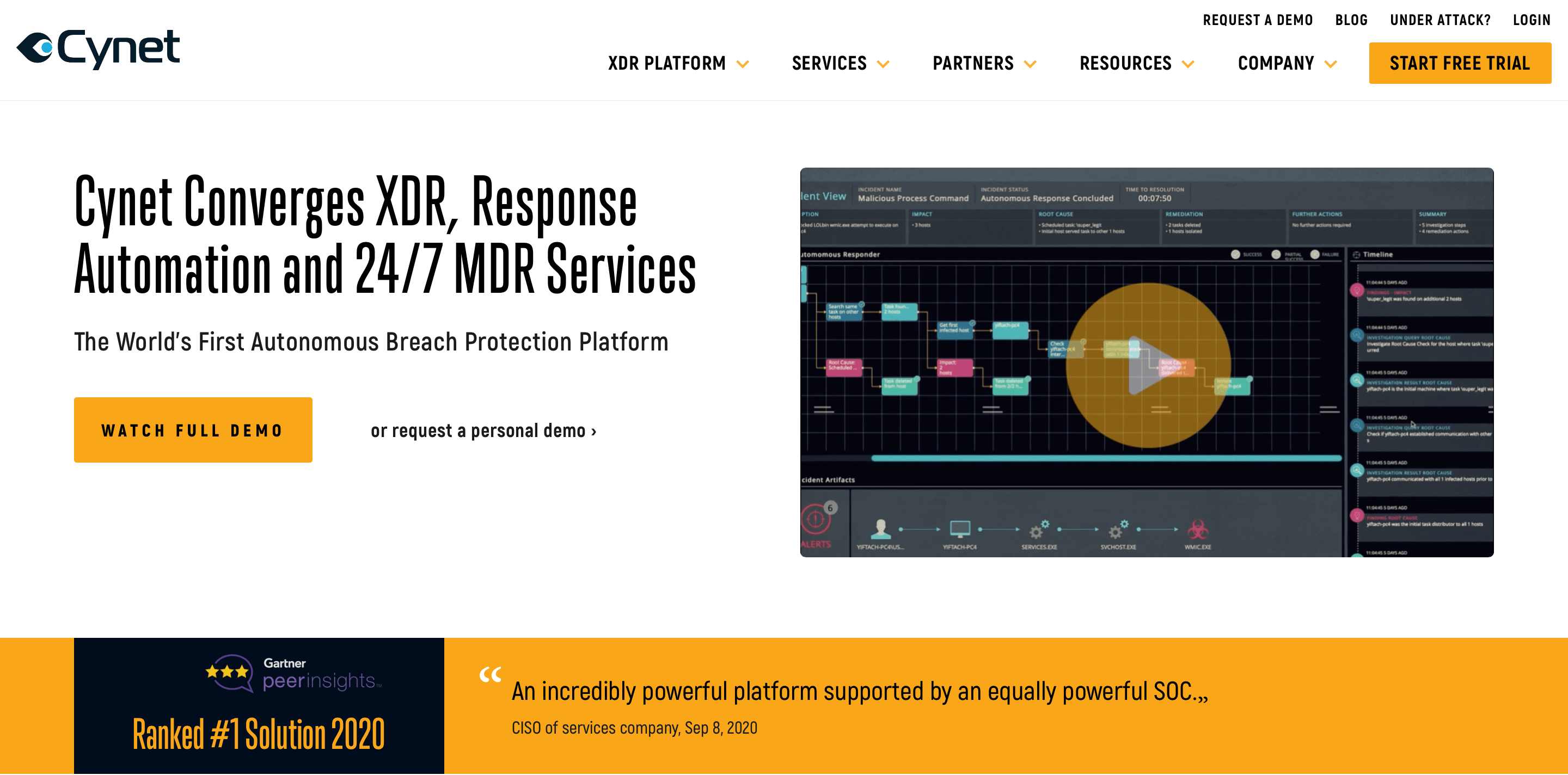
Best for: Mid-market organizations wanting comprehensive security without complexity
Cynet consolidates multiple security functions into a single platform: endpoint protection, network analytics, deception technology, and 24/7 managed detection and response.
Key Capabilities:
- Unified Security Platform: SIEM, EDR, NDR, and MDR in one solution
- Automated Investigation: AI correlates incidents across all security layers
- 24/7 SOC Services: Optional managed service component
- Rapid Deployment: Fastest time-to-value in the market
Real-World Impact: A manufacturing company replaced four separate security tools with Cynet, reducing their security stack costs by 60% while improving detection accuracy.
Deployment: 2-5 days for complete deployment across most environments.
Limitations: Less advanced AI compared to specialized vendors; may not scale for very large enterprises.
CrowdStrike Falcon — Cloud-Native Endpoint Intelligence

Best for: Organizations prioritizing advanced endpoint detection and response
CrowdStrike revolutionized endpoint security with cloud-native architecture and behavioral analysis. Their threat intelligence feeds from millions of endpoints globally provide unparalleled visibility into emerging threats.
Key Capabilities:
- Next-Gen Antivirus: AI-powered malware detection with minimal system impact
- Endpoint Detection & Response: Real-time threat hunting and investigation
- Threat Intelligence: Insights from analyzing 1+ trillion events weekly
- Zero-Downtime Deployment: Lightweight agent with cloud processing
Real-World Impact: During the 2020 SolarWinds attack, CrowdStrike was one of the first to identify the breach methodology, protecting thousands of customers.
Deployment: 1-7 days depending on environment size; can be deployed remotely.
Limitations: Primarily endpoint-focused; requires additional tools for comprehensive network coverage.
How to Choose the Right AI Threat Detection Platform
| Decision Factor | Why It Matters | What to Look For | Best Platform Match |
|---|---|---|---|
| Response Time Requirements | Every minute matters in breach containment | Autonomous response capabilities | Darktrace for fastest autonomous response |
| Network Complexity | Complex networks need specialized analysis | Deep network traffic analysis | Vectra AI for network-centric detection |
| Security Team Size | Small teams need consolidated tools | All-in-one platforms with managed services | Cynet for comprehensive coverage |
| Endpoint Priority | Many attacks start at endpoints | Advanced endpoint detection and global intelligence | CrowdStrike for endpoint-focused protection |
Red Flags to Avoid
Avoid These Common Mistakes:
- Deploying in full enforcement mode immediately (causes operational disruption)
- Choosing based solely on price (cheapest often means highest total cost)
- Ignoring integration requirements (silos reduce effectiveness)
- Skipping proof-of-concept testing (every network is different)
Bottom Line
Quick Decision Framework:
- Need autonomous protection? → Darktrace
- Complex network environment? → Vectra AI
- Want all-in-one simplicity? → Cynet
- Endpoint-focused strategy? → CrowdStrike
The question in 2026 is not whether your organization will face a sophisticated cyber attack, but how quickly you will detect and contain it. Traditional tools leave security teams reacting too late with too little context. AI-powered threat detection shifts the balance by identifying abnormal behavior early, reducing alert fatigue, and accelerating response at machine speed.
Each platform excels in different scenarios. Darktrace stands out where autonomous response and continuous self-learning are required across large, complex environments. Vectra AI is strongest in network-centric detection where lateral movement and internal reconnaissance are the primary risks. Cynet offers the fastest path to consolidated security operations for mid-market teams with limited staff. CrowdStrike Falcon remains a leader for organizations prioritizing endpoint visibility backed by large-scale threat intelligence.
The most successful teams treat AI threat detection as a capability, not a checkbox. They start in monitoring mode, validate results through pilots, integrate with existing workflows, and expand automation deliberately. Organizations that do this consistently see faster detection, fewer false positives, and lower breach impact.
Waiting for a breach to justify investment is the most expensive path forward. In a threat landscape defined by speed and stealth, prevention and early detection cost far less than recovery.


