Here is the uncomfortable truth. Nearly every serious cloud breach still comes down to access that should never have existed in the first place. In 2026, cloud environments move faster than humans can track. Temporary permissions linger, service accounts quietly accumulate power, and identities created during incidents are rarely revisited. What starts as a small shortcut during an outage often turns into a permanent backdoor months later.
This is no longer a tooling gap. It is an identity visibility problem. In modern cloud environments, infrastructure scales automatically, workloads appear and disappear, and permissions sprawl faster than traditional security reviews can keep up. Perimeter based security assumptions no longer apply when the real attack surface is identity and entitlement misuse. Without continuous insight into who can access what, when, and why, even well funded security teams are operating blind.
CIEM tools exist to close this gap. They bring visibility, context, and automation to cloud entitlements so access decisions stop being guesswork. This guide focuses on CIEM platforms that teams are actually using in production in 2026, what they do well, and where they fall short when exposed to real cloud complexity.
Quick Comparison: Top CIEM Tools at a Glance
| Tool | Current Status | Primary Strength | Deployment Time |
|---|---|---|---|
| Tenable Cloud Security (formerly Ermetic) | Active - Acquired by Tenable | Continuous monitoring & automated analysis | 2-4 weeks |
| Microsoft Entra Permissions Management (formerly CloudKnox) | Active - Part of Microsoft ecosystem | Deep Azure integration & hybrid environments | 1-2 weeks |
| Sonrai Security | Independent & active | Multi-cloud identity governance with patented analytics | 3-6 weeks |
| Lacework FortiCNAPP | Active - Enhanced CNAPP platform | Automated threat detection with CIEM capabilities | 1-3 weeks |
| Prisma Cloud CIEM | Active - GigaOm Leader & Outperformer | Enterprise-grade CNAPP with integrated CIEM module | 2-4 weeks |
| Wiz CIEM | Active - Rapid growth cloud security leader | Agentless deployment & risk-based prioritization | 1-2 weeks |
In-Depth Tool Analysis
Tenable Cloud Security (Formerly Ermetic) — "Continuous Cloud Security"
Current Status: Ermetic helps us fix over provisioned privledges in AWS, it's replaced our cloud trail log search, and we also utilize it's automated slack alerting for unusual cloud activity.
Best for: Organizations requiring continuous monitoring and automated remediation of cloud entitlements.
Key Capabilities:
- Real-time permission analysis across AWS, Azure, and GCP
- Automated rightsizing of over-privileged accounts
- Integration with existing SIEM and security workflows
- Advanced anomaly detection for suspicious access patterns
Deployment Reality: 2-4 weeks for full deployment, depending on cloud complexity. The Tenable acquisition has strengthened enterprise support but may introduce pricing changes.
What Users Actually Say: Teams appreciate the automated CloudTrail analysis replacement and Slack integration for real-time alerts. However, some report initial configuration complexity in multi-account environments.
Limitations: Requires careful tuning to reduce false positives; integration depth varies by cloud provider.
Microsoft Entra Permissions Management (Formerly CloudKnox Security) — "Enterprise Identity Powerhouse"
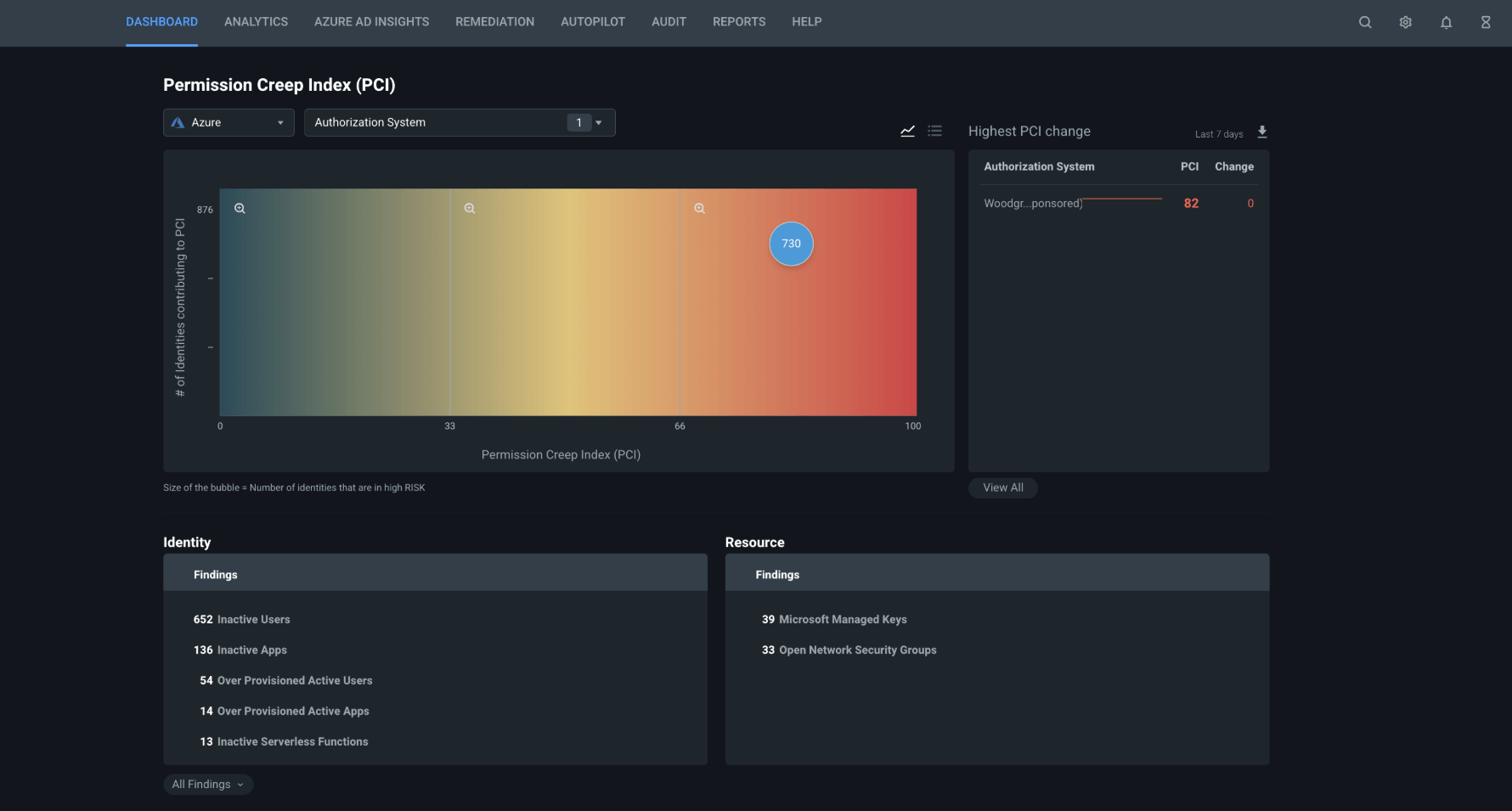
Current Status: Microsoft announced the acquisition of CloudKnox Security, a leader in Cloud Infrastructure Entitlement Management (CIEM) and it's now integrated as Microsoft Entra Permissions Management. It provides comprehensive visibility into permissions for all identities (both user and workload), actions, and resources across multi-cloud environments.
Best for: Organizations already invested in the Microsoft ecosystem or requiring hybrid cloud entitlement management.
Key Capabilities:
- Deep integration with Azure Active Directory and Microsoft 365
- Cross-cloud permission analysis (AWS, Azure, GCP)
- Automated least-privilege recommendations
- Built-in compliance reporting for major frameworks
Deployment Reality: 1-2 weeks for Azure-heavy environments; longer for complex multi-cloud setups. Microsoft's integration has improved stability but limited third-party tool flexibility.
What Users Actually Say: Seamless for Microsoft-centric organizations, but some find cross-cloud capabilities less robust than dedicated multi-cloud solutions.
Limitations: Best value comes with broader Microsoft licensing; standalone pricing can be complex.
Sonrai Security — "Multi-Cloud Identity Governance Master"
Current Status: Independent company with patented analytics and graphing technology that reveals every possible relationship between identities, their entitlements and the data they can access.
Best for: Enterprises with complex multi-cloud environments requiring deep identity relationship mapping.
Key Capabilities:
- Patented cloud graph technology for identity relationship mapping
- Advanced risk scoring based on data sensitivity and access patterns
- Comprehensive multi-cloud coverage (AWS, Azure, GCP, Kubernetes)
- Executive-level reporting and compliance dashboards
Deployment Reality: 3-6 weeks due to comprehensive discovery and mapping processes. The depth of analysis requires more initial setup but provides unmatched visibility.
What Users Actually Say: Praised for uncovering hidden permission relationships that other tools miss, but requires dedicated security engineering resources for optimal configuration.
Limitations: Higher learning curve; best suited for organizations with mature security teams.
Lacework FortiCNAPP — "Automated Workload Protection"
Current Status: Lacework FortiCNAPP has earned the 2025 SC Award for Best Cloud Workload Protection Solution, a prestigious honor recognizing excellence in securing cloud-native workloads.
Best for: Organizations prioritizing workload security with integrated CIEM capabilities.
Key Capabilities:
- Behavior-based anomaly detection for cloud workloads
- Integrated CIEM functionality within broader CNAPP platform
- Automated compliance monitoring and reporting
- Container and Kubernetes security with entitlement management
Deployment Reality: 1-3 weeks for basic deployment. The platform's strength in workload protection makes it valuable for DevSecOps teams.
What Users Actually Say: Strong automation reduces manual security overhead, though some prefer dedicated CIEM tools for complex entitlement scenarios.
Limitations: CIEM features are part of broader platform—may be overkill for organizations needing only entitlement management.
Prisma Cloud CIEM — "Enterprise-Grade Comprehensive Protection"
Current Status: GigaOm names Prisma Cloud a Leader and Outperformer in CIEM, showcasing excellence in securing cloud infrastructure and managing entitlements effectively. Prisma Cloud is the most complete Cloud Native Application Protection Platform (CNAPP) for code to cloud security in any cloud, multicloud, and hybrid environment.
Best for: Large enterprises requiring comprehensive cloud security with integrated CIEM capabilities across their entire development lifecycle.
Key Capabilities:
- Net-effective permissions calculation and analysis across AWS, Azure, and GCP
- Monitors for risky and unused entitlements with least-privilege recommendations
- Code-to-cloud security integration covering IaC, runtime, and compliance
- Advanced policy engine with custom rule creation
- Executive dashboards with risk quantification and business impact analysis
- Integration with major CI/CD pipelines and DevOps workflows
Deployment Reality: 2-4 weeks for comprehensive deployment. As a full CNAPP platform, implementation involves multiple security domains beyond just CIEM. Organizations often phase rollout by cloud provider or business unit.
What Users Actually Say: Enterprise customers praise the unified view across security domains, though some find the breadth of features requires dedicated training. The recent recognition as a CIEM leader validates its market position.
Limitations: Full value requires adopting the broader Prisma Cloud ecosystem; can be complex for organizations needing only CIEM functionality; enterprise-level pricing may not suit smaller organizations.
Wiz CIEM — "Developer-Friendly Risk-Based Prioritization"
Current Status: Wiz is the unified cloud security platform with prevention and response capabilities, enabling security and development teams to build faster and more securely. Wiz offers comprehensive visibility across cloud infrastructure without requiring agents, making it incredibly easy to deploy and scale.
Best for: Organizations prioritizing developer experience and risk-based security approaches in cloud-native environments.
Key Capabilities:
- Analyzes cloud entitlements and auto-generates least privilege policies across your cloud, to detect, prioritize, and remediate IAM risks
- Agentless, API-driven scanning across AWS, Azure, and GCP with complete inventory and full visibility of workloads, identities, and misconfigurations
- Security graph provides a clear view of vulnerabilities, misconfigurations, and potential attack paths in a unified interface
- Risk-based prioritization that correlates entitlements with actual security impact
- Developer-friendly interface with minimal friction for DevOps workflows
- Automatically maps relationships between resources
Deployment Reality: 1-2 weeks for initial deployment. The agentless approach makes it incredibly easy to deploy and scale, with minimal infrastructure changes required. Teams often see value within days of initial setup.
What Users Actually Say: Consistently praised for ease of deployment and developer adoption. Security teams appreciate the risk correlation features that help prioritize remediation efforts based on actual business impact rather than just permission count.
Limitations: As a newer entrant compared to legacy security vendors, may lack some enterprise compliance reporting features; pricing can scale quickly with cloud resource growth.
Additional Considerations
Important Note About Pricing: Most CIEM tools don't publish transparent pricing. Expect enterprise discussions starting around $50,000-$100,000 annually for meaningful deployments, with costs scaling based on cloud resources and users monitored.
Deployment Checklist:
- Inventory all cloud accounts and subscription models
- Assess existing identity providers and directory services
- Plan for initial permission discovery phase (can take 1-4 weeks)
- Prepare for potential service disruptions during least-privilege enforcement
- Budget for training and change management across security and DevOps teams
How to Choose Your CIEM Tool: Strategic Framework
| Evaluation Criteria | Why This Matters | What to Investigate | Red Flags to Avoid |
|---|---|---|---|
| Multi-Cloud Coverage | Most enterprises use 2+ cloud providers | Native API integration depth, not just surface-level support | Tools claiming "universal support" without provider-specific features |
| Integration Ecosystem | CIEM must work with existing security stack | SIEM, SOAR, ticketing system connectors and API quality | Vendors promising "easy integration" without technical documentation |
| Automation Capabilities | Manual entitlement management doesn't scale | Policy-based auto-remediation, approval workflows, emergency access procedures | Tools requiring constant manual intervention for routine tasks |
| Risk Intelligence | Not all permissions carry equal risk | Context-aware risk scoring, data sensitivity mapping, business impact analysis | Generic permission reporting without risk context |
The Bottom Line: Making Your CIEM Decision
The CIEM market has matured significantly, but choosing the right tool depends heavily on your specific environment and organizational constraints.
Choose Microsoft Entra Permissions Management if: You're Microsoft-centric and need seamless Azure integration with decent multi-cloud coverage.
Choose Tenable Cloud Security if: You want continuous monitoring with strong automation and don't mind vendor lock-in with a security-focused company.
Choose Sonrai Security if: You have complex multi-cloud environments and need the deepest possible visibility into identity relationships, regardless of deployment complexity.
Choose Lacework FortiCNAPP if: You're building a comprehensive cloud security program and want workload protection integrated with entitlement management.
Choose Prisma Cloud CIEM if: You're a large enterprise needing comprehensive cloud security across the entire development lifecycle, and you want industry-leading CIEM capabilities integrated with broader security controls.
Choose Wiz CIEM if: You prioritize developer experience, need rapid deployment, and want risk-based prioritization that correlates entitlements with actual security impact rather than just permission volume.
Start Your Evaluation With These Questions:
- How many cloud accounts and what types do you currently manage?
- What's your current process for granting and revoking cloud access?
- How long does it take to answer "who has access to our production databases" today?
- What's your budget for both tool licensing and implementation resources?
CIEM is no longer optional for organizations running serious workloads in the cloud. In 2026, access risk is the dominant cause of breaches, and entitlement sprawl is the silent driver behind it. The most effective teams treat CIEM as core security infrastructure, not an add on for audits or compliance reviews. They use it to answer hard questions quickly, reduce standing permissions aggressively, and enforce least privilege without breaking production.
There is no single best CIEM tool for every organization. Microsoft centric environments benefit from deep native integration. Complex multi cloud estates need graph based visibility. Developer driven teams succeed when tooling minimizes friction and prioritizes real risk over raw permission counts. What matters most is alignment with how your teams actually work and how fast you can move from insight to remediation.
If your organization cannot confidently answer who has access to critical cloud resources right now, you already have a problem. The right CIEM platform will not just surface that risk, it will help you continuously reduce it. The wrong one will generate reports no one acts on. Choose based on visibility, automation, and operational fit, because cloud access mistakes do not announce themselves until it is too late.


