Most teams discover identity and misconfiguration risk during an incident review, not from scheduled audits. Working across different tech companies, we have seen CNAPPs prevent issues like an overly permissive IAM role on a production account, a container image with a critical CVE pushed to a public registry, and a Terraform misconfiguration that opened an S3 bucket to the internet. Cloud security spending is projected to reach $213 billion in 2025 and $240 billion in 2026, according to Gartner's 2025 security spending forecast. Three platforms consistently deliver strong coverage and buyer value.
A verified market signal shows why CNAPPs matter now. The average breach reached $4.44 million globally in 2025, per IBM's Cost of a Data Breach Report 2025, while US breaches hit a record $10.22 million. Identity, misconfigurations, and cloud workload risk continue to dominate cloud incidents, as summarized in CSA's Top Threats to Cloud Computing 2024 and Sysdig's 2025 Cloud-Native Security and Usage Report. These three CNAPPs excel at agentless visibility, identity-aware risk reduction, and developer-to-runtime coverage. You will learn when each tool is the best fit, what to watch for, and how to avoid hidden costs.
Orca Security
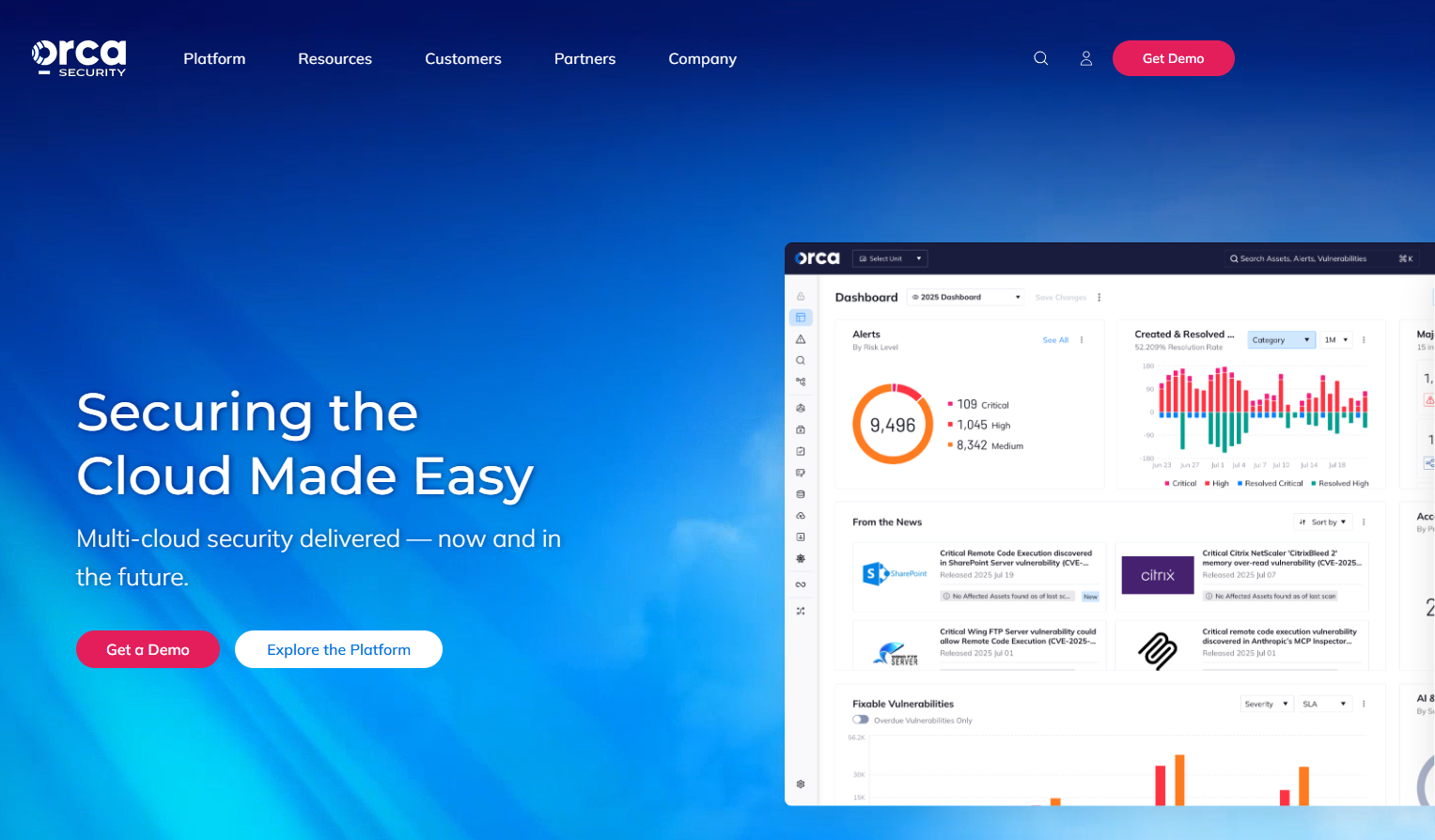
Agentless CNAPP with broad coverage across posture, workload, identity, data, and API security. Focuses on unified visibility and context to prioritize real attack paths.
Best for: Security teams that want fast, agentless coverage across AWS, Azure, GCP, and Kubernetes with strong risk prioritization.
Key Features:
- Agentless discovery and scanning across cloud resources, VMs, containers, serverless, and data stores.
- Unified risk context with attack path analysis, prioritizing the 1 percent of issues that matter most.
- CIEM and DSPM alongside CSPM and CWPP in one platform, plus compliance reporting and IaC checks.
Why we like it: In the startup ecosystem, Orca's agentless onboarding cuts weeks of coordination and still surfaces identity plus workload risks in one view, which saves hours during triage.
Notable Limitations: Users report occasional alert noise that needs tuning, performance hiccups in specific compliance modules, and requests for deeper policy customization in some areas.
Pricing: Pricing not publicly available. Available as a private offer in major cloud marketplaces; contact the seller for a custom quote.
Uptycs
Hybrid-cloud CNAPP that combines CNAPP and XDR to give telemetry-driven visibility from developer devices and CI to containers and cloud runtime.
Best for: Teams that want a single console and data lake for cloud, Kubernetes, servers, and endpoints, with developer pipeline visibility and runtime detections.
Key Features:
- CNAPP plus XDR in one UI and data lake, correlating cloud, container, server, and endpoint telemetry.
- Kubernetes and container supply chain controls with image policy enforcement and runtime detections.
- Identity and posture coverage across multi-cloud, with compliance reporting and threat hunting.
Why we like it: After helping startups scale, consolidating dev-to-runtime signals into one queryable backend shortens investigations and cuts tool sprawl.
Notable Limitations: Reviews note a learning curve for advanced queries and APIs, UI complexity in some modules, and that documentation depth can vary by feature.
Pricing: Pricing not fully public. Marketplace listings indicate private offers for CNAPP and add-ons; contact Uptycs for a custom quote.
Ermetic (now part of Tenable Cloud Security)
Identity-first CNAPP known for deep CIEM, now the core of Tenable Cloud Security after the acquisition closed on October 2, 2023.
Best for: Organizations prioritizing identity and entitlement risk reduction, with needs across CIEM, CSPM, and development-time checks.
Key Features:
- Identity-first CNAPP with graph-based CIEM for human and machine identities.
- CSPM and workload context with risk-based prioritization and clear remediation guidance.
- Shift-left coverage for IaC and CI/CD with multicloud posture.
Why we like it: Identity sprawl is the root cause in many cloud incidents. Strong CIEM plus posture analysis helps teams fix toxic combinations that lead to lateral movement.
Notable Limitations: Buyers mention initial setup complexity in large multi-cloud estates, some alert tuning to reduce low-priority noise, and that pricing can be a consideration for small teams.
Pricing: Pricing not publicly available. Contact Tenable for a custom quote.
CNAPP Tools Comparison: Quick Overview
| Tool | Best For | Pricing Model | Highlights |
|---|---|---|---|
| Orca Security | Agentless, fast coverage across clouds and K8s | Custom quote, marketplace private offers | Unified CSPM, CWPP, CIEM, DSPM with attack path context |
| Uptycs | Unified CNAPP plus XDR, dev-to-runtime visibility | Custom quote, marketplace private offers | Single data lake and console across cloud, K8s, servers, endpoints |
| Ermetic, now Tenable Cloud Security | Identity-first CNAPP with strong CIEM | Custom quote | Deep entitlement analysis with multicloud posture and IaC checks |
CNAPP Platform Comparison: Key Features at a Glance
| Tool | Identity and CIEM | Data Security (DSPM) | Kubernetes and Container Security |
|---|---|---|---|
| Orca Security | Yes, identity risk and policy analysis | Yes, sensitive data discovery and risk context | Yes, image scanning, K8s posture, runtime risk signals |
| Uptycs | Yes, identity and posture insights | Emerging coverage tied to platform modules | Yes, supply chain controls, runtime detections, incident response |
| Ermetic, now Tenable Cloud Security | Yes, graph-based CIEM is a core strength | Capabilities integrated into Tenable Cloud Security | IaC scanning, K8s posture, and multicloud visibility |
CNAPP Deployment Options
| Tool | Cloud API | On-Premise | Integration Complexity |
|---|---|---|---|
| Orca Security | Yes | Not publicly documented | Low for API onboarding, tuning may be moderate in large estates |
| Uptycs | Yes | Limited components possible, platform is primarily SaaS | Moderate, broader telemetry means more knobs to configure |
| Ermetic, now Tenable Cloud Security | Yes | Not publicly documented | Moderate, identity graphing at scale benefits from planned onboarding |
CNAPP Strategic Decision Framework
| Critical Question | Why It Matters | What to Evaluate |
|---|---|---|
| Do we need agentless coverage, runtime agents, or both? | Scanning gaps and overhead drive cost and blind spots | Supported services, depth of findings, performance impact |
| How do we manage identity and entitlements across clouds? | Identity issues rank as top cloud threats | CIEM depth, graph context, machine identity coverage |
| Can the platform correlate dev, cloud, and runtime? | Faster investigations and fewer tools | Single data model, CI/CD integrations, forensic depth |
| What is the total cost of ownership at our scale? | Telemetry, storage, and services affect budget | Pricing metric, marketplace options, support and PS costs |
CNAPP Solutions Comparison: Pricing and Capabilities Overview
| Organization Size | Recommended Setup | Cost Estimate |
|---|---|---|
| Startup, under 250 employees | Agentless CNAPP baseline with CIEM and compliance, add K8s posture | Custom quote, not publicly available |
| Mid-market, 250-2,000 employees | CNAPP plus container runtime insights, IaC in CI, identity risk workflows | Custom quote, not publicly available |
| Enterprise, 2,000+ employees | Full CNAPP, deep CIEM for human and machine identities, DSPM, threat hunting | Custom quote, not publicly available |
Problems & Solutions
-
Problem: Excessive permissions and identity sprawl raise breach risk. Reports show identity is a leading cloud threat, and unused or risky permissions are widespread, as highlighted by CSA's Top Threats and Sysdig's 2025 report takeaways.
- How Orca helps: CIEM plus attack path context ties identities to exposed assets and vulnerable workloads.
- How Uptycs helps: Correlates identity signals with workload and endpoint telemetry to flag risky combinations from dev to cloud. Findings about identity blind spots in real environments are a recurring theme in Sysdig's research.
- How Ermetic, now Tenable Cloud Security, helps: Identity-first CNAPP with graph-based CIEM reduces toxic combinations in multicloud environments, with the acquisition confirmed by Cooley's transaction note.
-
Problem: Misconfigurations and internet exposure keep causing incidents, which amplifies breach costs that reached $4.44 million on average globally in 2025 per IBM's breach report.
- How Orca helps: Agentless posture scanning across accounts and services, plus policy-aligned compliance, reduces open exposure. User reviews highlight breadth of visibility and fast onboarding on G2's Orca page.
- How Uptycs helps: Posture and vulnerability findings flow into one console with detection content mapped to MITRE ATT&CK, and Kubernetes supply chain controls, with product updates reported in industry news like PR Newswire.
- How Ermetic, now Tenable Cloud Security, helps: Multicloud posture mapped to identity context and IaC checks to stop risky deployments, aligned with the acquisition integration described in GlobeNewswire's closing announcement.
-
Problem: Short-lived containers and fast CI/CD make runtime drift hard to manage. Attackers automate reconnaissance, which increases the need for continuous detection, as noted in Sysdig's 2025 report.
- How Orca helps: Container image analysis and K8s posture help block risky images and misconfigurations before runtime.
- How Uptycs helps: Adds runtime detections, threat hunting, and forensics for containers and hosts, with marketplace listings for CNAPP and runtime sensors on AWS Marketplace.
- How Ermetic, now Tenable Cloud Security, helps: Integrates IaC scanning, posture, and identity context so risky changes are caught earlier, with buyer feedback about strengths and setup tradeoffs on G2's Tenable Cloud Security page.
Choosing Your CNAPP: A Practical Bottom Line
The biggest CNAPP mistakes happen when teams assume posture, identity, and workload security are separate checklists. Cloud security spending is projected to reach $213 billion in 2025 and grow to $240 billion in 2026, per Gartner's spending forecast, and breach costs remain significant at $4.44 million on average globally in 2025, per IBM's report. If you want fast coverage with strong context and minimal operational lift, Orca Security is a solid agentless choice that buyers rate highly on G2. If you want one platform and data lake across cloud, Kubernetes, servers, and endpoints, Uptycs' CNAPP plus XDR model is compelling, with continual feature launches covered by PR Newswire. If identity risk is your top priority, Ermetic's capabilities, now in Tenable Cloud Security, are well suited for CIEM-first programs, with the acquisition confirmed by Cooley's deal coverage. Always request a hands-on trial, validate coverage for your top cloud services, and pressure test alert quality against recent incidents before you buy.


