Most teams discover identity compromise during an incident postmortem, not from the SIEM dashboard. Working across different tech companies, the biggest gaps we still see are basic, technical signals that go unnoticed, like OAuth consent abuse in Microsoft 365, Kerberoasting attempts against service accounts, and anomalous session token reuse across SaaS. The global average breach cost reached $4.44 million in 2025 according to IBM's Cost of a Data Breach Report, while US organizations faced a record $10.22 million average. Stolen or misused credentials remain a common thread in breaches, with 22 percent of breaches involving credential abuse as the initial access vector per the 2025 Verizon DBIR. This guide will help you focus on what cuts detection time and response toil.
Identity attacks dominate modern incidents, and 88 percent of basic web application attacks involved stolen credentials, per the 2025 Verizon DBIR. From a long list of platforms in this space, we narrowed to four that consistently delivered coverage and time to value across hybrid identity, SaaS, and cloud. You will learn where each platform fits, what it actually detects, how it responds, and where its tradeoffs show up in real deployments.
Delinea Identity Threat Protection
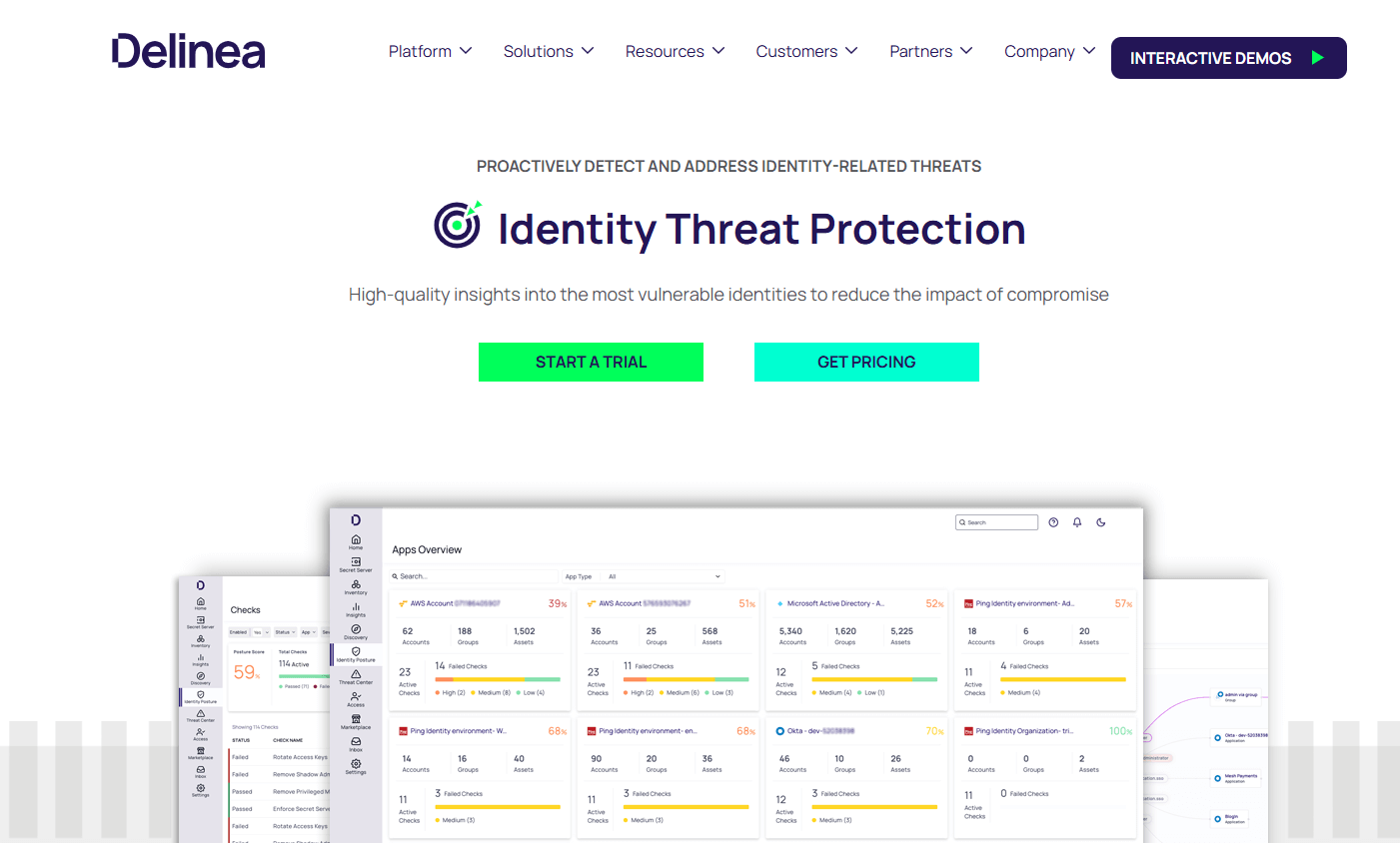
Delinea folds ITDR into its broader PAM platform. Per Delinea documentation, it monitors federated and local identities, highlights risky access pathways, and triggers guided or automated responses across SaaS and hybrid infrastructure.
Best for: PAM-led teams that want ITDR embedded in a single platform spanning privileged accounts, AD, Entra ID, and SaaS.
Key Features:
- Continuous detection of identity misconfigurations and anomalous behavior across identity systems and SaaS.
- Graph-style visualization of access pathways to expose risky blast radius.
- AI-driven risk insight to prioritize remediation.
- Automated or guided actions to contain MFA bombing, brute force, and takeover attempts.
- Unified admin in a cloud-native platform that sits alongside PAM.
Why we like it: If you are already standardizing on PAM, adding ITDR where your privileged workflows already live reduces swivel chair and speeds containment during off-hours.
Notable Limitations:
- Users report complex setup and higher latency in some cloud workflows, with complaints about support quality in certain cases, as seen in select community threads and reviews on G2 and on the sysadmin subreddit discussions cited by users' experiences.
- Mixed feedback on documentation depth and upgrade experience in enterprise environments per multiple G2 entries.
Pricing: Pricing not publicly available. Contact Delinea for a custom quote.
Grip Security ITDR 2.0
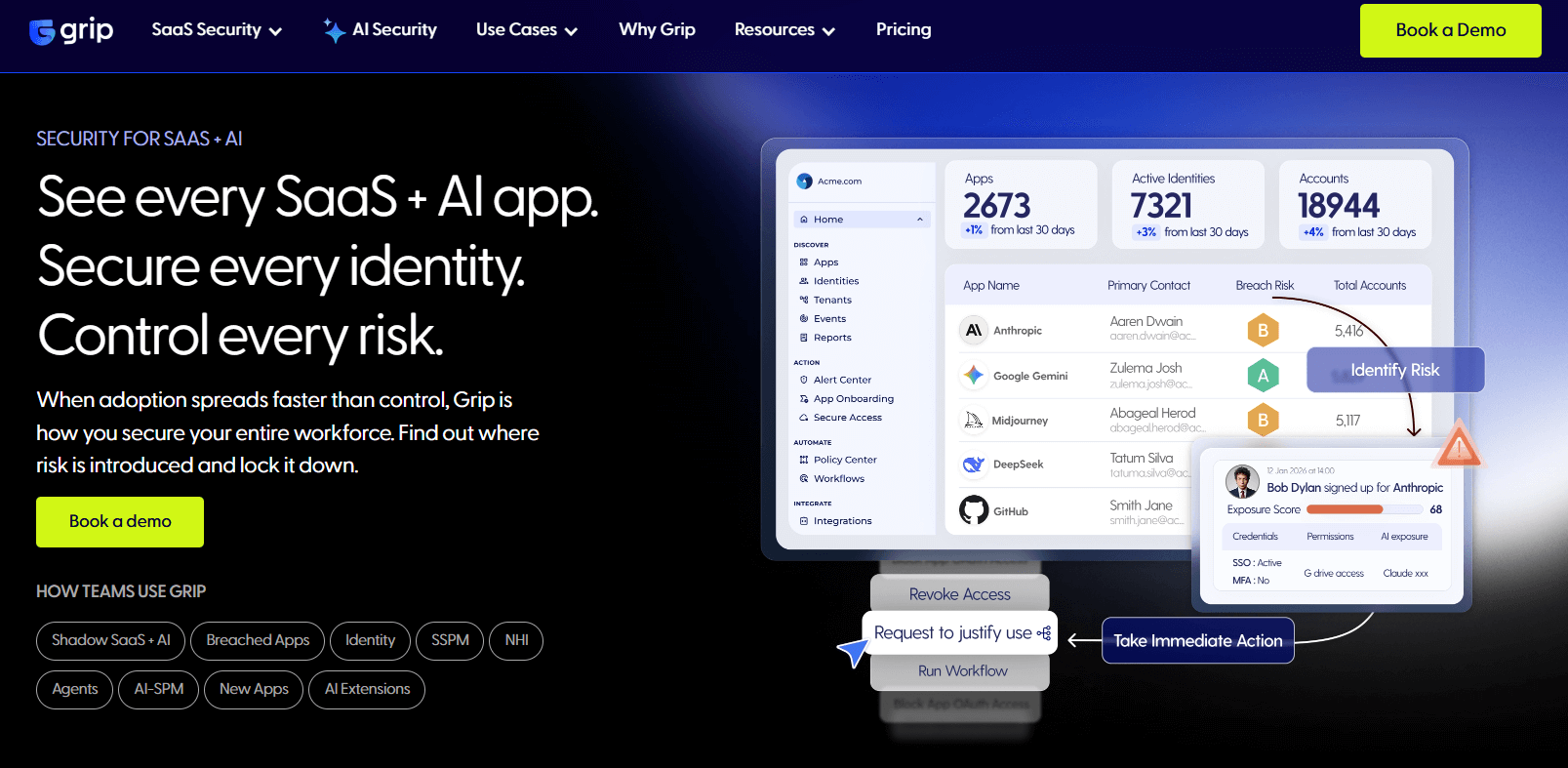
Grip focuses ITDR on SaaS, including unmanaged and shadow apps, with automated response and prevention features like risky OAuth grant detection and blast radius mapping. Its 2025 release emphasized prevention plus detection for SecOps.
Best for: SaaS-first organizations battling shadow IT, risky OAuth grants, and identity sprawl across managed and unmanaged apps.
Key Features:
- Real-time detection across all SaaS, including unsanctioned apps and high-risk browser extensions, per vendor materials.
- Detection of malicious OAuth grants and automated one-click or policy-driven responses, as described in launch coverage on GlobeNewswire.
- Identity attack surface management and blast radius visualization to speed triage.
- Integrations with SIEM and SOAR for workflow handoff.
Why we like it: The SaaS-centric signal set, especially OAuth grant monitoring and unmanaged app discovery, fills a blind spot that classic identity tools miss.
Notable Limitations:
- Limited public buyer feedback compared with longer-tenured vendors, and reviews mention setup complexity and a learning curve on G2.
- Young category coverage means deeper diligence for data sources, playbooks, and tuning.
Pricing: Pricing not publicly available. Contact Grip Security for a custom quote. Funding and momentum have been covered by TechCrunch.
Vectra AI ITDR
Vectra extends its detection stack to identity, correlating AD, Microsoft Entra ID, SaaS, network, and cloud signals with AI-based triage and automated actions. Per vendor materials, it targets real attacker behaviors to cut noise.
Best for: Enterprises that want correlated identity detection across hybrid estates with strong coverage for AD, Entra ID, M365, AWS, and network.
Key Features:
- Identity attack detection for AD and Entra ID, plus M365 and AWS coverage, with AI correlation across surfaces.
- Prioritized detections and guided investigations to speed mean time to respond.
- Automated or customized response actions, and broad ecosystem integrations.
- Independent news notes expanding partnerships for cloud-delivered detections, such as integration with ZIA reported by Investor's Business Daily.
Why we like it: Strong coverage depth across identity plus adjacent surfaces reduces blind spots and lowers triage noise in high-volume SOCs.
Notable Limitations:
- Reviewers cite higher cost and reporting gaps relative to expectations in several G2 reviews.
- Some deployments require careful sizing and architecture to control total cost of ownership, per buyer feedback on G2.
Pricing: AWS Marketplace listings show starting prices such as "Vectra AI Platform Standard" at $499 per month and "Complete" at $1,299 per month, while some listings are private offer or per IP or per user based, so enterprise pricing varies by scope (AWS Marketplace).
CheckRed ITDR
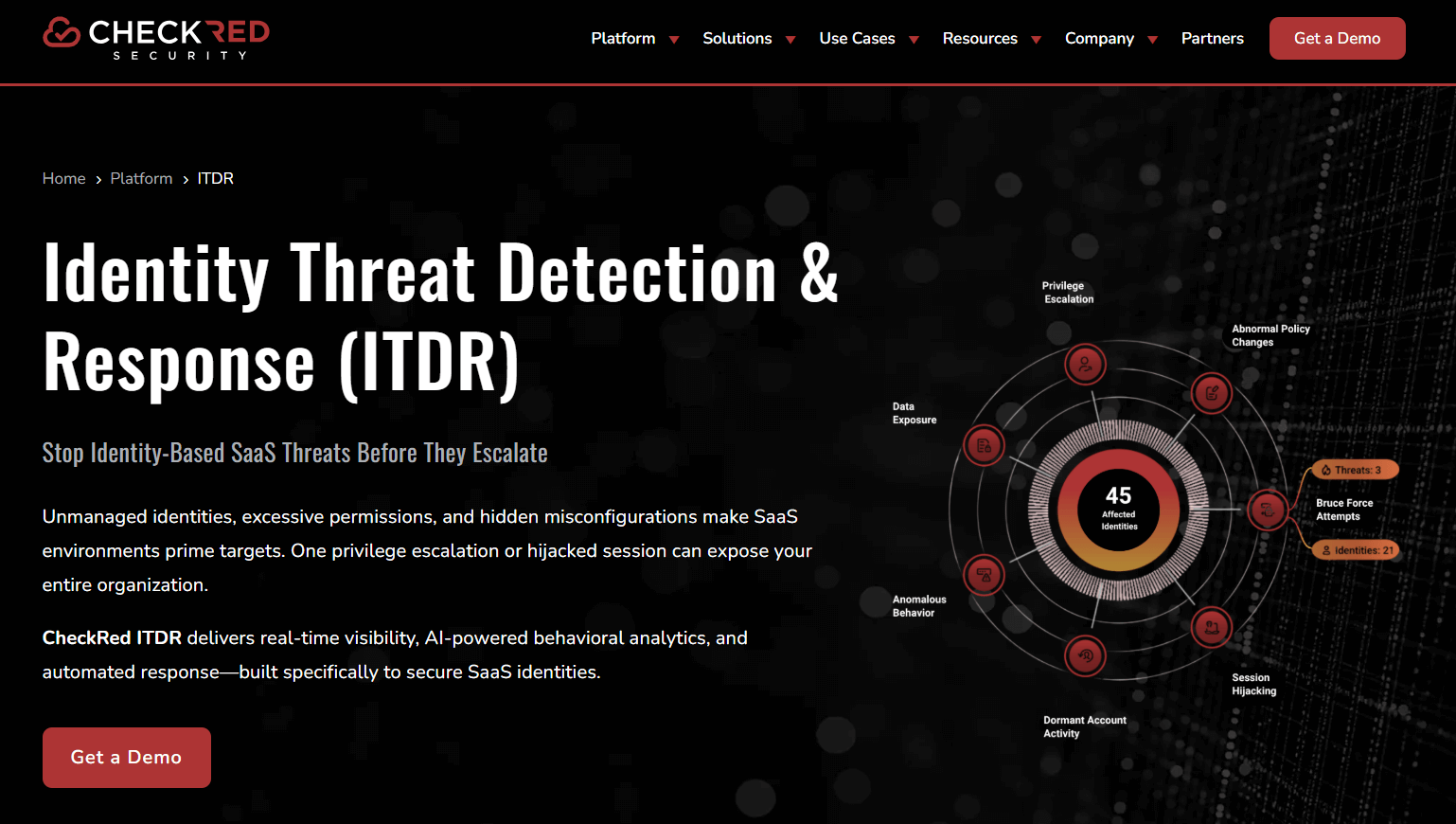
CheckRed adds ITDR to a broader SaaS and cloud posture platform, focusing on real-time SaaS identity analytics, behavior baselining, and automated responses across major apps.
Best for: Lean teams that want SaaS identity monitoring tied to SSPM and cloud posture in a single console.
Key Features:
- Real-time behavioral analytics for SaaS identities and continuous monitoring across apps.
- Alerts for privilege escalation, session hijacking patterns, dormant account reactivation, and abnormal policy changes.
- Context-rich investigations that map threats to specific users and permissions, with integrations to SIEM and SOAR.
Why we like it: Tying ITDR signals to posture management simplifies investigations where misconfiguration and identity misuse are intertwined.
Notable Limitations:
- Fewer third-party reviews compared to category leaders, and some feedback mentions false positives and deployment complexity on G2.
- Limited public benchmarks and analyst coverage, so buyers should run a proof of value with defined success metrics.
Pricing: Pricing not publicly available. Contact CheckRed for a custom quote.
ITDR Tools Comparison: Quick Overview
| Tool | Best For | Pricing Model | Highlights |
|---|---|---|---|
| Delinea Identity Threat Protection | PAM-centric programs that want ITDR fused into privileged workflows | Quote based | Identity graph and automated remediation inside a PAM platform |
| Grip Security ITDR 2.0 | SaaS-first and shadow IT heavy environments | Quote based | Detects malicious OAuth grants, unmanaged apps, and risky browser extensions |
| Vectra AI ITDR | Hybrid estates needing correlated signals across AD, Entra ID, M365, AWS, and network | Marketplace and quote based | Marketplace pricing exists, and integrations with cloud security stacks |
| CheckRed ITDR | SaaS identity analytics linked to posture management | Quote based | Real-time SaaS identity monitoring and incident context with posture data |
ITDR Platform Comparison: Key Features at a Glance
| Tool | Identity Anomaly Detection | OAuth Grant and SaaS Risk | Automated Response |
|---|---|---|---|
| Delinea Identity Threat Protection | Yes, across federated and local identities | Focus on SaaS and identity pathway risk | Yes, guided and automated actions |
| Grip Security ITDR 2.0 | Yes, real time across managed and unmanaged SaaS | Yes, detects malicious OAuth grants and risky extensions | Yes, one-click and policy driven |
| Vectra AI ITDR | Yes, AD and Entra ID with network and cloud correlation | Strong M365 and AWS coverage per platform materials | Yes, native and integrated actions |
| CheckRed ITDR | Yes, behavior baselining for SaaS users | Yes, SaaS identity risks tied to posture data | Yes, via integrations and playbooks |
ITDR Deployment Options
| Tool | Cloud API | On-Premise | Integration Complexity |
|---|---|---|---|
| Delinea Identity Threat Protection | Yes | Available within broader Delinea platform options | Moderate if expanding beyond PAM footprint |
| Grip Security ITDR 2.0 | Yes | Primarily cloud delivered | Low to moderate, depends on SaaS coverage and IdP access |
| Vectra AI ITDR | Yes | Supported for hybrid estates | Moderate, plan sizing for identity, network, and cloud |
| CheckRed ITDR | Yes | Cloud first | Low to moderate, depends on SSPM and SIEM/SOAR tie in |
ITDR Strategic Decision Framework
| Critical Question | Why It Matters | What to Evaluate |
|---|---|---|
| Do we detect malicious OAuth grants and unmanaged SaaS access? | Consent phishing and token abuse are frequent in M365, per recent Microsoft guidance. | OAuth grant detection, browser extension risk, unmanaged app coverage, response actions. |
| How do we handle AD and Entra ID techniques like Kerberoasting and relay? | AD abuse and Kerberos attacks persist, and Microsoft outlines concrete detections and mitigations in 2025 guidance (Microsoft). | Service account monitoring, SPN analytics, DC focused detections, enrichment with PAM and EDR. |
| Can we cut MFA fatigue risk? | MFA prompt bombing has driven high profile breaches, as discussed by Microsoft Entra and covered by Ars Technica. | Impossible travel, session anomalies, MFA abuse heuristics, response like temporary step up or session kill. |
| What is the response path from alert to containment? | Mean time to respond is a top cost driver per IBM's 2025 report. | Native actions, playbooks, IdP integration, SOAR handoffs, rollback of risky grants. |
ITDR Solutions Comparison: Pricing and Capabilities Overview
| Organization Size | Recommended Setup | Cost Estimate |
|---|---|---|
| SMB with heavy Microsoft 365 | Vectra AI ITDR starter plus M365 coverage, or Grip for SaaS focused signals | From $499 per month via AWS Marketplace for selected Vectra packages, scope varies |
| Mid market hybrid AD and SaaS | Delinea ITP attached to PAM, or Vectra AI ITDR for correlated hybrid coverage | Quote based for Delinea, Vectra enterprise pricing varies and includes private offers |
| Enterprise with shadow IT | Grip ITDR 2.0 for unmanaged SaaS risks plus IdP and SOAR integration, or Vectra AI ITDR for broad coverage | Quote based for Grip, Vectra mix of marketplace and private offers |
Problems & Solutions
-
Problem: OAuth consent phishing and token abuse in M365 and Entra ID, where users grant malicious apps high impact scopes. Microsoft details active campaigns and controls such as app consent policies and publisher verification in its guidance and threat research (Microsoft Learn, Microsoft Security Blog).
- Delinea Identity Threat Protection: Surfaces anomalous consent and identity pathway risk, then applies guided or automated remediation tied to PAM policies.
- Grip Security ITDR 2.0: Detects malicious OAuth grants across managed and unmanaged apps and provides one click response and revocation per launch notes.
- Vectra AI ITDR: Correlates identity signals from Entra ID and M365 with network and cloud behavior for high confidence triage, and integrates with enforcement paths.
- CheckRed ITDR: Focuses on SaaS identity behavior, flags abnormal policy changes and privilege escalation, and routes revocation actions through SIEM or SOAR.
-
Problem: MFA fatigue and session hijacking, where attackers spam prompts or pivot to weaker fallbacks. Microsoft recommends number matching and policy tuning, and press coverage shows the real world impact.
- Delinea Identity Threat Protection: Detects abnormal login patterns and can trigger risk based actions, aligned with PAM controls for privileged identities.
- Grip Security ITDR 2.0: Monitors SaaS sessions in real time, detects anomalous logins, and can automatically revoke sessions in targeted apps.
- Vectra AI ITDR: Correlates MFA abuse indicators with lateral movement signals across identity, cloud, and network, then automates containment.
- CheckRed ITDR: Flags suspicious logins and dormant account reactivation and supports immediate token revocation via playbooks.
-
Problem: AD and Kerberos focused attacks like authentication relay and Kerberoasting that precede domain dominance. Microsoft's 2025 guidance outlines detections and mitigations for modern AD risks.
- Delinea Identity Threat Protection: Monitors service accounts and access pathways, with PAM based least privilege to shrink exposure.
- Grip Security ITDR 2.0: Less focused on classic AD internals, better as a complement for SaaS identity and OAuth risks.
- Vectra AI ITDR: Strong AD and Entra ID coverage with correlated detections that surface real attacker behaviors, then orchestrate a response.
- CheckRed ITDR: Primarily SaaS, used as a companion to AD centric controls in hybrid estates.
Conclusion: Picking the Right ITDR Fit
Credentials drive breach impact and cost, and 22 percent of breaches in 2025 involved credential abuse as the initial access vector per the 2025 Verizon DBIR. Pair that with a global average breach cost of $4.44 million (and $10.22 million for US organizations) in IBM's 2025 report, and ITDR moves from nice to have to essential. If you are PAM led, Delinea's approach keeps privileged workflows and identity detections in one place. If shadow SaaS is your reality, Grip's SaaS first ITDR closes the OAuth and unmanaged app gap. If you want broad hybrid correlation, Vectra AI stands out and has marketplace options to pilot quickly. If you need SaaS identity context tied to posture, CheckRed brings ITDR and SSPM together. Start with your dominant identity risks, run a two week proof with clear success metrics, and buy the tool that cuts your investigation time in half.


