Your APIs are under attack right now. While you are reading this, automated bots are probing your endpoints, testing authentication logic, abusing business workflows, and mapping your data exposure. By 2026 APIs have become the dominant attack surface for modern applications, accounting for a rapidly growing share of web traffic and security incidents as organizations shift to microservices, mobile apps, and third-party integrations. Security teams are seeing sustained increases in automated API abuse, credential stuffing, and logic-based attacks that bypass traditional controls entirely.
The problem is not theoretical. A growing number of high-profile breaches are traced back to unsecured or poorly monitored APIs, often months after attackers first gained access. Legacy security tools such as firewalls and intrusion detection systems were designed for monolithic applications and perimeter defenses. They lack the context to understand API behavior, authorization intent, and abuse patterns. Attackers no longer need to break in when APIs willingly hand over sensitive data.
APIs are also multiplying faster than they can be secured. Dev teams ship new endpoints daily. Shadow APIs persist long after the services that created them are forgotten. Third-party integrations quietly expand the attack surface beyond what most security inventories can track. By 2026 many organizations acknowledge that APIs represent both their most valuable digital asset and their least protected one. That reality is driving a shift toward dedicated API security platforms that can discover, monitor, and defend APIs continuously across the full lifecycle.
Quick Comparison: Top API Security Tools at a Glance
| Tool | Primary Strength | Best Use Case | Deployment Speed |
|---|---|---|---|
| 42Crunch | Developer-first security integration | DevSecOps teams embedding security in CI/CD | Moderate |
| Salt Security | AI-infused full lifecycle protection | Enterprises needing comprehensive threat detection | Fast |
| Noname Security | Proactive vulnerability discovery | Teams wanting preemptive security measures | Fast |
| Cequence Security | Advanced threat mitigation | Large enterprises with complex API ecosystems | Moderate |
| Traceable AI | Real-time behavioral analysis | Organizations focused on anomaly detection | Fast |
| Wallarm | All-in-one platform approach | Companies wanting unified API and app security | Moderate |
| Data Theorem | Comprehensive API inventory and discovery | Organizations with unknown API sprawl | Fast |
42Crunch API Security Platform — Security-First Development
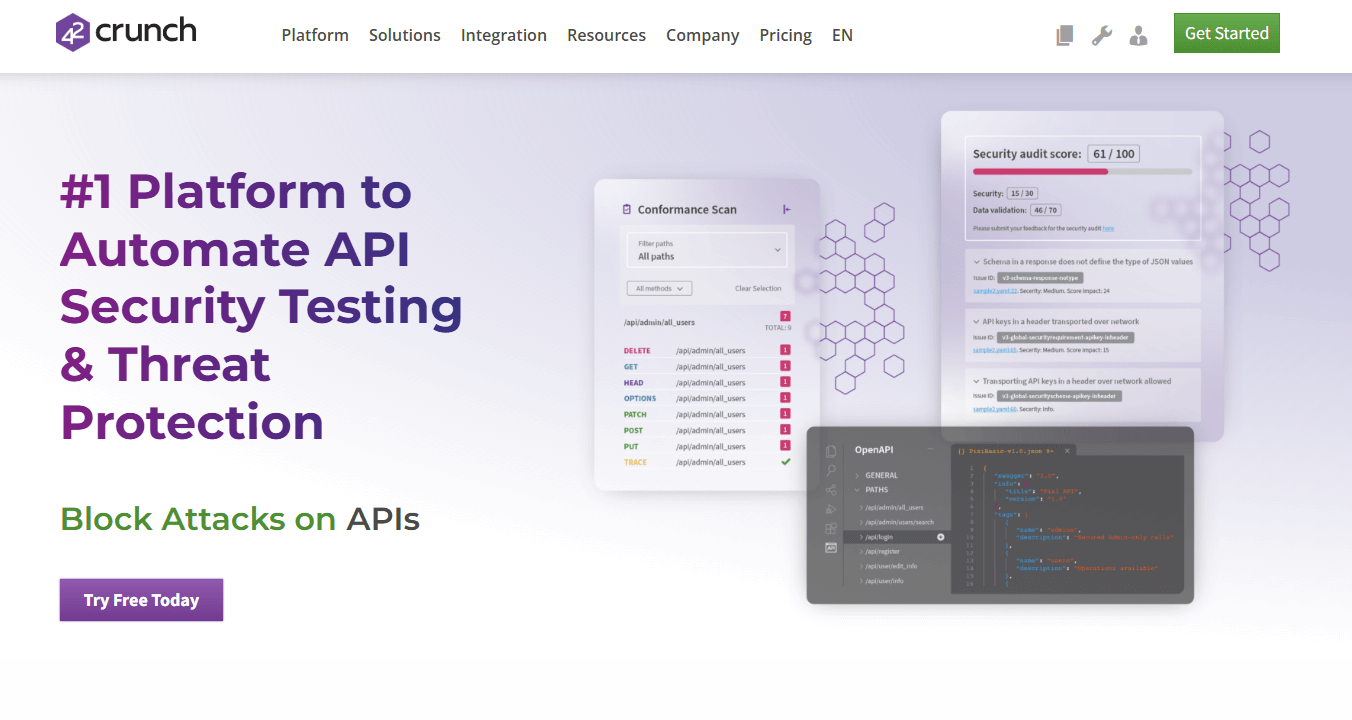
Best for: Development teams that want to embed security directly into their API lifecycle without slowing down delivery.
42Crunch stands out with its developer-first approach. Developer-First API Security Platform makes it easy for developers to build and automate security into their API development pipeline speeding up the delivery cycle as opposed to slowing it down. The platform offers immediate zero-day API threat prevention with purpose-built real-time validation and blocking.
Key Features:
- 200+ static analysis security checks for OpenAPI format conformance, authentication, authorization, transport, data validation, and API security best practices
- Real-time API protection with transaction-level inspection
- CI/CD integration for shift-left security
- OpenAPI specification security auditing
Deployment Considerations:
The platform integrates seamlessly with existing development workflows, though initial setup requires careful configuration to align with your development processes.
When to Choose 42Crunch:
Your development team is already using OpenAPI specifications and wants security tools that enhance rather than hinder their velocity.
Salt Security — AI-Powered Attack Prevention
Best for: Organizations that need sophisticated threat detection across their entire API ecosystem.
Salt Security leverages the industry's largest API data lake to power its threat detection capabilities. Through its unique API Context Engine (ACE) architecture, the Salt platform provides design analysis in pre-production, discovers all APIs, pinpoints and stops API attackers, and provides remediation insights. The company holds the only granted patent for using AI to identify and prevent API attacks.
Key Features:
- Behavioral analysis using machine learning
- Complete API discovery and compliance monitoring
- Runtime protection against sophisticated attacks
- Integration with SOC/SIEM tools
Deployment Considerations:
Quick deployment with cloud-native architecture, though organizations need to plan for initial learning period as AI models adapt to their specific API patterns.
When to Choose Salt Security:
You're dealing with complex, high-volume API traffic and need AI-powered insights to detect sophisticated attack patterns that rule-based systems miss.
Noname Security — Proactive Risk Management

Best for: Security teams that prefer to identify and remediate vulnerabilities before they're exploited.
Noname Security focuses on getting ahead of threats through comprehensive visibility and proactive vulnerability management. The platform excels at discovering shadow APIs and identifying misconfigurations that could lead to breaches.
Key Features:
- Comprehensive API discovery and inventory
- Vulnerability and misconfiguration detection
- Risk assessment and prioritization
- Integration with existing security workflows
Deployment Considerations:
Straightforward setup with intuitive dashboards, though maximum value requires integration with existing vulnerability management processes.
When to Choose Noname Security:
Your organization has a mature security program and wants to extend proactive vulnerability management to your API ecosystem.
Cequence Security — Enterprise-Grade Threat Protection
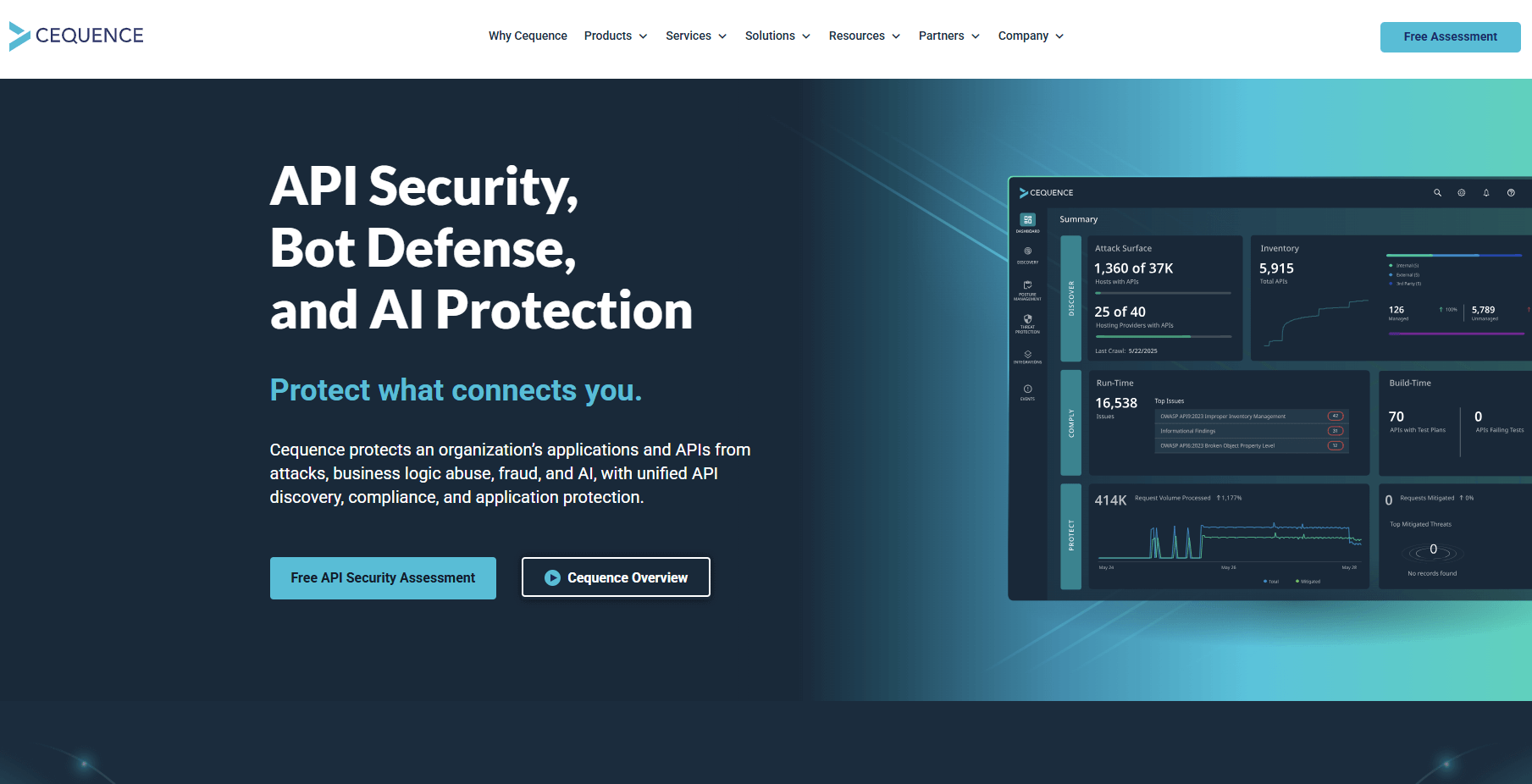
Best for: Large enterprises with complex API architectures requiring comprehensive threat mitigation.
Cequence Security provides robust protection against various API attack vectors, with particular strength in detecting and mitigating automated attacks and bot traffic targeting APIs.
Key Features:
- Advanced bot detection and mitigation
- Real-time threat intelligence
- Comprehensive API attack protection
- Scalable enterprise deployment
Deployment Considerations:
More complex setup due to enterprise-focused feature set, but offers extensive customization options for large-scale deployments.
When to Choose Cequence Security:
You're running APIs at enterprise scale and need sophisticated protection against advanced persistent threats and automated attack campaigns.
Traceable AI — Behavioral Intelligence Platform
Best for: Organizations that want deep insights into API behavior patterns and anomaly detection.
Traceable is a powerful API security solution that protects APIs in real-time using artificial intelligence and machine learning. It provides detailed insights on API traffic and behavioral patterns that help identify both security threats and operational issues.
Key Features:
- Advanced API mapping and discovery
- Behavioral anomaly detection
- Real-time threat monitoring
- Detailed analytics and insights
Deployment Considerations:
User-friendly deployment with strong analytics capabilities, though organizations should plan for data integration to maximize insights.
When to Choose Traceable AI:
Your team values data-driven security decisions and wants detailed visibility into how your APIs are being used and potentially abused.
Wallarm — Unified Security Platform
Best for: Organizations seeking a consolidated approach to API and application security.
Wallarm's latest report demonstrates their deep understanding of current API threat landscapes. The platform provides comprehensive protection for both APIs and web applications from a single interface.
Key Features:
- Unified API and application security
- Automatic threat detection and blocking
- Integration with DevOps workflows
- Real-time security monitoring
Deployment Considerations:
Moderate setup complexity but offers comprehensive coverage, making it ideal for organizations wanting to consolidate security tools.
When to Choose Wallarm:
You want to reduce security tool sprawl and prefer a single platform that covers both API and broader application security needs.
Data Theorem — Discovery and Inventory Excellence
Best for: Organizations struggling with API sprawl and unknown security exposure.
Data Theorem API Secure can inventory every API that exists within a network, cloud, application, or any other target. That makes it a great choice for organizations that want to beef up their API security, but don't know where to start or even how many APIs they are using.
Key Features:
- Comprehensive API discovery and inventory
- Automated vulnerability detection
- Continuous security monitoring
- DevOps pipeline integration
Deployment Considerations:
Fast deployment with emphasis on automation, ideal for organizations that need immediate visibility into their API landscape.
When to Choose Data Theorem:
You suspect you have shadow APIs or simply don't have a complete inventory of your API attack surface.
Strategic Selection Framework
| Decision Factor | Why It Matters | What to Evaluate | Red Flags to Avoid |
|---|---|---|---|
| Integration Complexity | Poor integration creates security gaps | Native CI/CD support, API-first architecture | Tools requiring extensive custom development |
| Detection Capabilities | Modern attacks bypass traditional rules | AI/ML-powered analysis, behavioral detection | Solutions relying solely on signature-based detection |
| Scalability Requirements | API traffic grows exponentially | Cloud-native architecture, elastic scaling | Solutions with hard traffic limits or licensing constraints |
| Time to Value | Security teams are resource-constrained | Quick deployment, immediate visibility | Tools requiring months of configuration or tuning |
The Bottom Line: Choose Based on Your Biggest Pain Point
The best API security tool isn't the one with the most features—it's the one that solves your most critical business problem:
- If your developers are struggling with security integration: Choose 42Crunch for its developer-first approach
- If you're facing sophisticated attacks: Salt Security's AI capabilities provide the most advanced threat detection
- If you don't know what APIs you have: Data Theorem's discovery capabilities are industry-leading
- If you want consolidated security management: Wallarm offers the most comprehensive unified platform
- If you need deep behavioral insights: Traceable AI provides unmatched analytics and anomaly detection
In 2026 API security is no longer a niche concern or a future roadmap item. It is a core requirement for protecting customer data, maintaining regulatory compliance, and sustaining digital business velocity. The most effective API security programs focus first on visibility, knowing exactly which APIs exist, how they are used, and what data they expose. From there they layer behavioral analysis, real-time threat detection, and tight integration with development workflows.
No single tool is right for every organization. Developer-led teams benefit most from platforms that embed security directly into CI/CD pipelines. Enterprises with high-volume API traffic and active attackers need runtime protection and behavioral analysis that can detect abuse without relying on static rules. Organizations struggling with API sprawl should prioritize discovery and inventory before advanced controls.
The difference between success and failure is not the number of features but the speed at which risk is reduced. Teams that treat API security as a continuous capability rather than a one-time deployment are the ones that turn APIs from a liability into a competitive advantage. In today’s environment your APIs will either be your easiest path to growth or your fastest path to a breach. The tools you choose decide which outcome you get.


