Most teams discover non-human identity sprawl during a Friday night incident review, not from a quarterly identity audit. Working across different tech companies, we have seen three patterns repeat: expired cloud access keys hardcoded in CI/CD, orphaned Kubernetes service accounts with admin scopes, and AI agent tokens pasted into Slack or Google Docs. These are not edge cases, they are the day to day realities of NHIM that break least privilege and blow up audit timelines.
The average breach hit $4.88M in 2024, according to IBM's Cost of a Data Breach Report, and stolen or compromised credentials remained a leading initial vector, which makes NHIM worth board attention today, not next quarter. Machine and agent identities also now dwarf human users in many environments, with Sysdig reporting machine identities outnumber humans 40,000 to 1 in real cloud telemetry.
Defakto
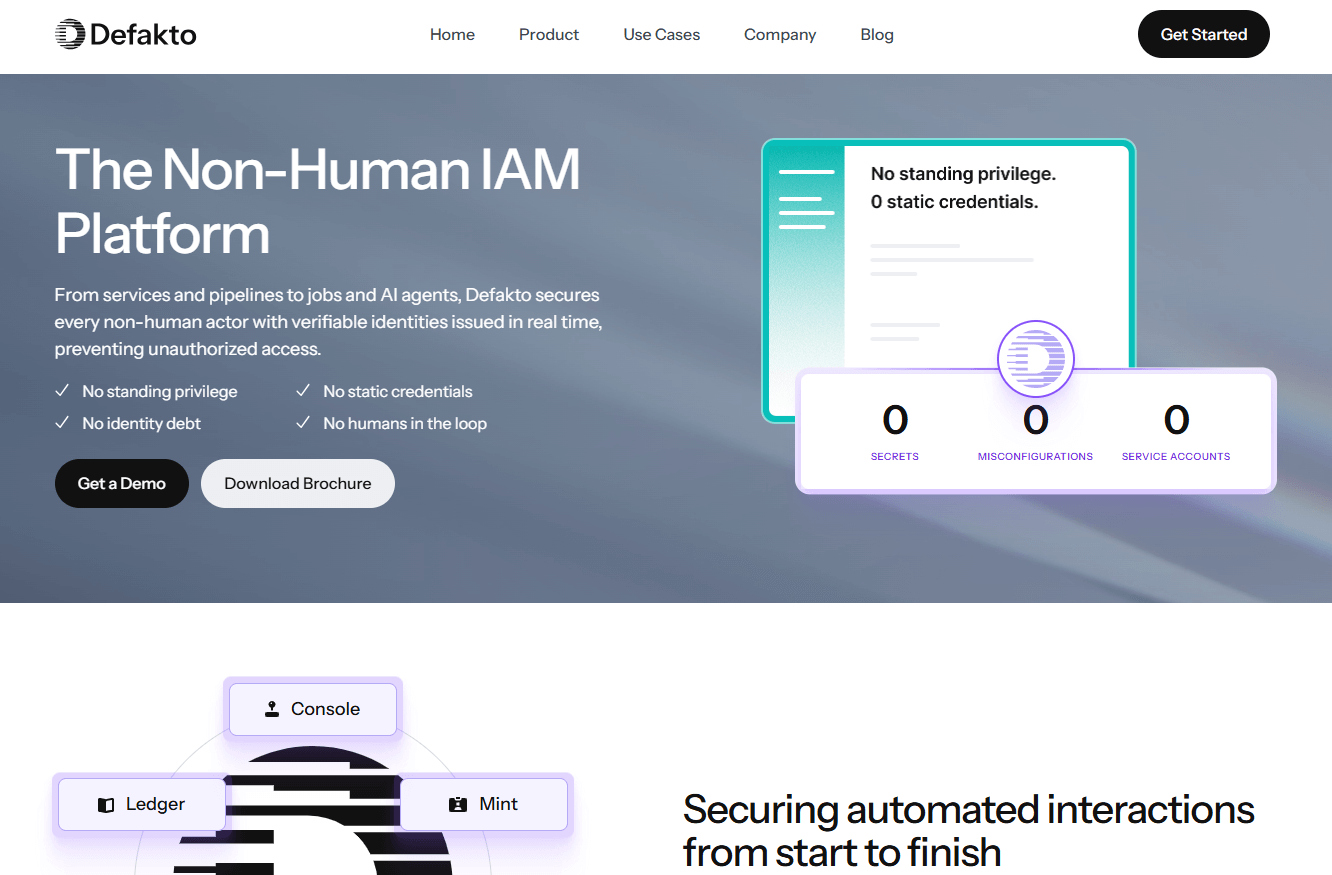
Defakto issues short-lived, verifiable identities to non-human actors, replacing static secrets and standing privileges with runtime identity. It unifies discovery, issuance, access right-sizing, CI/CD coverage, and AI agent identity in a single control plane.
- Best for: Security and platform teams that want a secretless model for services, pipelines, and AI agents, with standards-aligned identities.
- Key Features: Real-time identity issuance for workloads and jobs, no long-lived secrets. Continuous discovery and governance of non-human identities across cloud and on-prem. Secretless CI/CD that injects ephemeral identity per job or stage. Access right-sizing with policy-bound, time-scoped privileges. AI agent identity security with full attribution and audit.
- Why we like it: Moving from keys to verifiable identity cuts blast radius and admin overhead. Defakto's secretless CI/CD approach maps cleanly to developer workflows without vault sprawl.
- Notable Limitations: Younger vendor with fewer third-party reviews than incumbents. Pricing not publicly listed. Feature depth in edge environments may require a proof of value.
- Pricing: Pricing not publicly available. Contact Defakto for a custom quote.
Entro
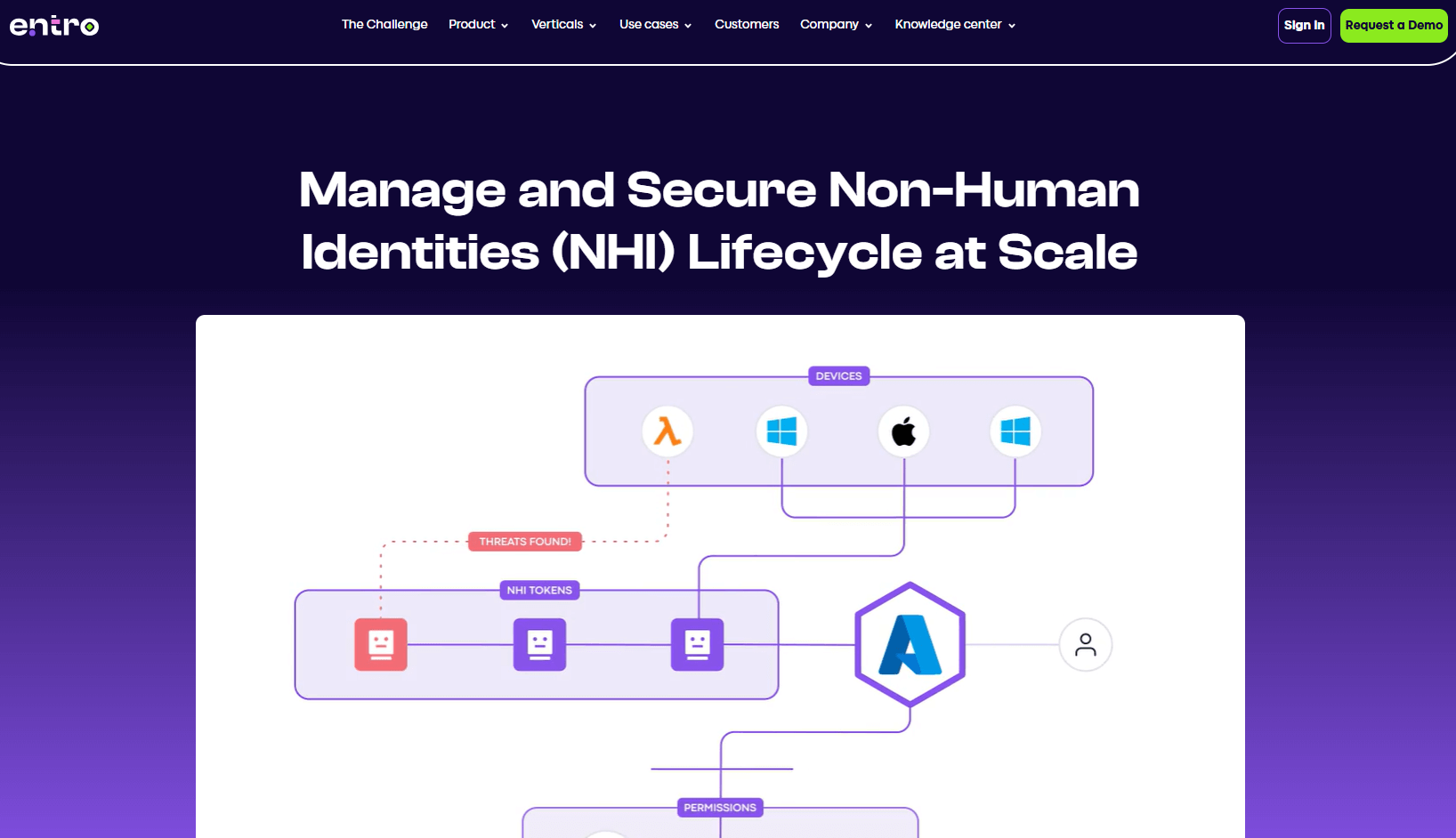
Entro discovers, classifies, and monitors non-human identities and secrets, then automates lifecycle controls, posture, detection, and remediation. It emphasizes ownership attribution and continuous risk scoring across clouds, code, CI/CD, and SaaS.
- Best for: Enterprises wrestling with leaked or over-privileged tokens across repos, chat, pipelines, and vaults who want detection and response plus cleanup at scale.
- Key Features: Discovery and inventory of NHIs and secrets across code, cloud, CI/CD, and SaaS. Ownership attribution that maps each identity or secret to a responsible team. Posture analysis for misconfigurations, permission drift, and orphaned access. NHIDR detection and response for anomalous NHI behaviors. Guided remediation including rotation, vaulting, and decommissioning.
- Why we like it: Entro's breadth across collaboration tools, repos, and pipelines surfaces the real places secrets leak, and its remediation workflows reduce manual ticket churn.
- Notable Limitations: Reviews note a learning curve for advanced configuration and reporting customization. Requests for deeper RBAC and multi-tenancy controls appear in user feedback. Some alerting and webhook configurations may need vendor assistance.
- Pricing: AWS Marketplace lists an Entro Security Starter Pack at $50,000 per year. Enterprise pricing may vary by scope, request a private offer.
Oasis Security

Oasis auto-discovers non-human identities, adds context and ownership, detects posture and threats, then automates lifecycle and remediation. The company has also introduced agentic access governance models for AI.
- Best for: Identity and security teams standardizing NHIM and AI agent governance across cloud, SaaS, and CI/CD with policy-driven remediation.
- Key Features: Unified inventory of NHIs with usage, consumers, resources, and ownership context. Posture detection, anomaly detection, and attack fingerprinting with AuthPrint. Out-of-the-box remediation plans and lifecycle workflows. Policy-based governance mapped to compliance frameworks.
- Why we like it: The ownership discovery focus plus prescriptive remediation playbooks help close the gap between finding issues and fixing them inside change windows.
- Notable Limitations: Newer entrant with a smaller body of public reviews than legacy IAM tools. Feature set is evolving quickly, so evaluate roadmap fit for regulated environments. Enterprise pricing is typically negotiated.
- Pricing: AWS Marketplace lists an Oasis Starter Pack at $50,000 per year. For enterprise tiers, contact Oasis or request a private offer.
Saviynt (Non-Human Identity)
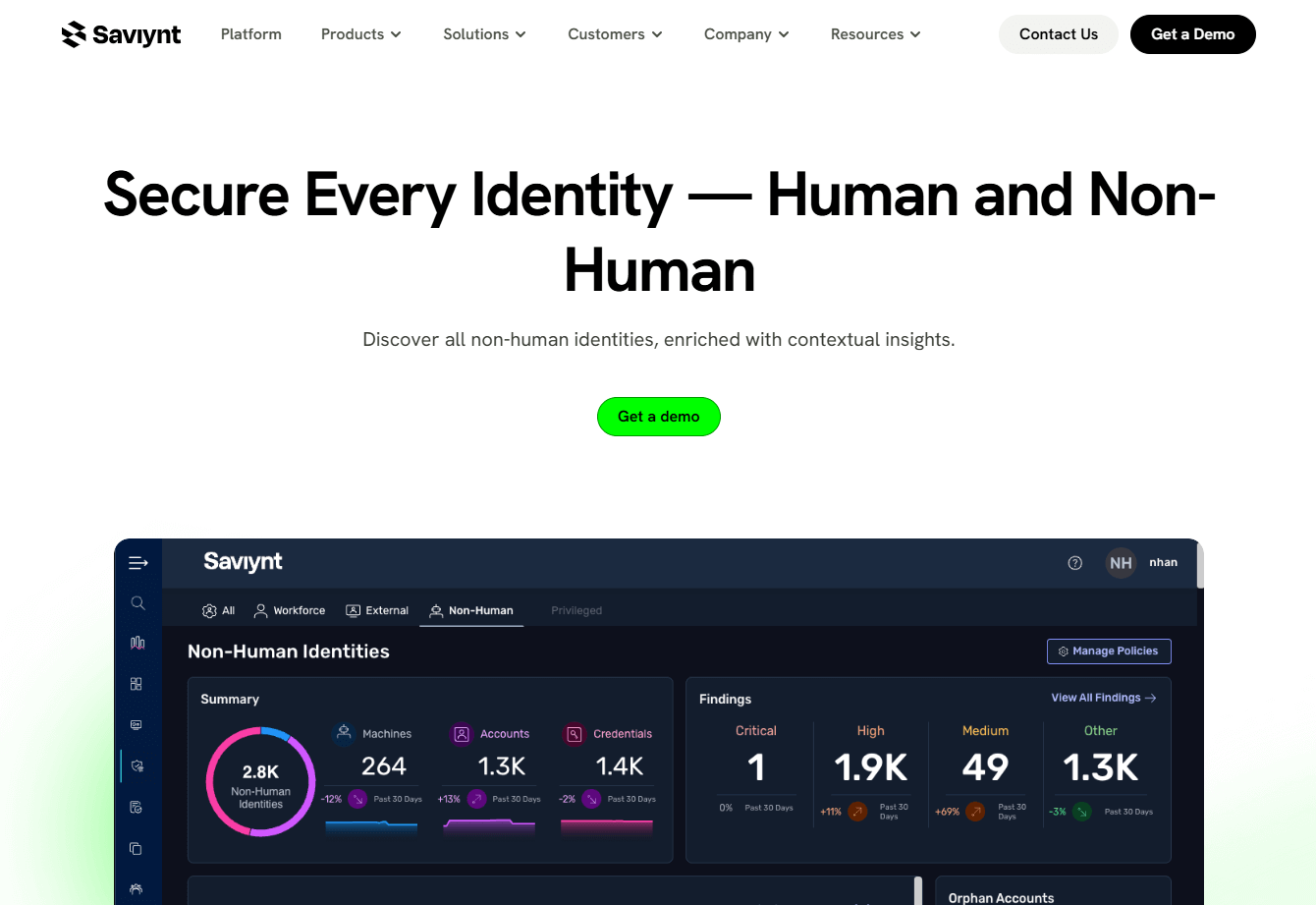
Saviynt extends its converged identity platform to non-human identities, providing real-time inventory, contextual insights, risk detection, lifecycle tracking, and AI-guided remediation.
- Best for: Organizations standardizing human and non-human governance on one identity security platform with strong audit and compliance posture.
- Key Features: Real-time inventory and unified NHI dashboard with contextual insights. Risk detection and prioritized remediation with identity security posture. Timeline visualization of NHI activity and lifecycle events. Integrated governance across PAM, IGA, and application access.
- Why we like it: One platform for human and non-human identities simplifies audits, reduces overlap between teams, and brings NHI into existing governance workflows.
- Notable Limitations: G2 reviewers cite a learning curve and complex configurations for some integrations. Onboarding applications can be time-consuming in large estates. Some ServiceNow workflows require expert configuration.
- Pricing: AWS Marketplace lists Saviynt Identity Cloud modules at $100,000 per year and a Saviynt MCP Server listing at $10,000 per year. Private offers are common.
NHIM Tools Comparison: Quick Overview
| Tool | Best For | Pricing Model | Highlights |
|---|---|---|---|
| Defakto | Secretless identities for services, pipelines, and AI agents | Custom quote | Ephemeral, verifiable identities replace secrets |
| Entro | Secrets and NHI sprawl across code, chat, and CI/CD | AWS Marketplace, custom | NHIDR detection, ownership attribution, guided remediation |
| Oasis Security | Policy-driven NHIM and agentic AI governance | AWS Marketplace, custom | Ownership discovery, AuthPrint threat fingerprinting, playbooks |
| Saviynt (NHI) | Unified governance across human and non-human | AWS Marketplace, custom | Converged identity platform, ISPM, timeline view |
NHIM Platform Comparison: Key Features at a Glance
| Tool | Discovery & Inventory | Posture & Risk | Detection & Response |
|---|---|---|---|
| Defakto | Continuous discovery of non-human actors | Right-sizing and least privilege by policy | Real-time issuance and audit with verifiable identity |
| Entro | Cross-cloud, code, CI/CD, and SaaS | Misconfig and drift analysis, ownership attribution | NHIDR anomaly detection and scalable remediation |
| Oasis Security | Inventory with usage and ownership context | Policy-based governance and posture checks | Scout anomaly detection and remediation plans |
| Saviynt (NHI) | Real-time NHI inventory with context | Identity posture, prioritized risks | AI-guided remediation and activity timeline |
NHIM Deployment Options
| Tool | Cloud API | On-Premise | Noted Integrations |
|---|---|---|---|
| Defakto | Yes | Yes | Kubernetes, service meshes, CI/CD, SIEM |
| Entro | Yes | Yes | GitHub, GitLab, Bitbucket, Slack, Teams, Google Workspace |
| Oasis Security | Yes | Yes | AWS, Azure, GCP, HashiCorp Vault, ServiceNow |
| Saviynt (NHI) | Yes | Connectors/agents | PAM, IGA, CrowdStrike, SAP, application connectors |
NHIM Strategic Decision Framework
| Critical Question | Why It Matters | What to Evaluate |
|---|---|---|
| Can it remove static secrets from pipelines? | Keys in code and CI/CD drive breaches and outages | Secretless options, ephemeral identity, coverage across jobs |
| Does it map every NHI to an owner? | Remediation stalls without ownership | Ownership discovery, attestation workflows, ticketing integrations |
| How does it prioritize risky identities? | NHIs outnumber humans by orders of magnitude | Usage-aware risk scoring, permission drift detection, toxic combos |
| What is the remediation path? | Alerts without fix steps waste time | One-click rotation, decommission, right-sizing, policy as code |
NHIM Solutions Comparison: Pricing & Capabilities Overview
| Organization Size | Recommended Setup | Investment Guidance |
|---|---|---|
| Mid-market with CI/CD and SaaS sprawl | Entro Starter Pack or Oasis Starter Pack via AWS Marketplace | $50,000 per year each per AWS Marketplace |
| Enterprise consolidating on identity platform | Saviynt Identity Cloud modules via AWS Marketplace | $100,000 per module per year |
| Platform teams driving secretless automation | Defakto pilot in high-risk pipelines and services | Pricing not publicly available, contact vendor |
Problems & Solutions
Problem: Static credentials in cloud email and token systems become a single point of failure
- Context: The U.S. Cyber Safety Review Board called the 2023 Microsoft cloud email intrusion "preventable," citing a cascade of errors and stolen keys, which spotlights why machine identity controls must be first class.
- How tools help:
- Defakto replaces long-lived keys with short-lived, verifiable identities, so there are no standing tokens to steal.
- Entro detects exposed or misused secrets and rotates them with ownership attribution, shrinking blast radius.
- Oasis finds leaked credentials, ties them to owners, and offers out-of-the-box remediation plans to decommission or rotate.
- Saviynt brings stolen credential risk into identity posture, then guides remediation through its converged platform.
Problem: Certificate and machine identity outages disrupt customer services
- Context: Research found 77% of organizations experienced at least two significant outages from expired certificates within 24 months, highlighting the operational cost of unmanaged machine identities.
- How tools help:
- Defakto's standards-based identity issuance shifts away from manual cert tracking to runtime identity.
- Entro flags idle, orphaned, or over-scoped NHIs and secrets, helping teams remove brittle credentials.
- Oasis automates lifecycle, including rotation and safe decommissioning, to avoid expiration-driven outages.
- Saviynt inventories NHIs and provides timeline views for lifecycle tracking and audit readiness.
Problem: Agentic AI explodes non-human identities faster than governance can keep up
- Context: Machine identities outnumber humans at extreme ratios in real cloud telemetry, and leaders expect identity-based attacks to rise as agents proliferate.
- How tools help:
- Defakto issues scoped, time-bound identities to AI agents and logs every action for accountability.
- Entro discovers shadow agents across collaboration tools and CI/CD, with NHIDR for real-time anomalies.
- Oasis provides agentic access governance with policy enforcement and ownership for agents and tools.
- Saviynt extends identity posture management to AI and non-human identities with guided remediation.
Problem: Secrets leak in collaboration platforms and shared docs
- Context: Enterprises increasingly find programmatic credentials in chat and documents, which expands the attack surface beyond code and cloud. Entro announced coverage for Google Workspace to detect and govern secret exposure in common apps.
- How tools help:
- Entro scans Slack, Teams, and Workspace for secrets and maps each finding to owners for quick fixes.
- Oasis detects leaked credentials with its Scout capability and fingerprints likely attackers to cut false positives.
- Defakto's secretless model removes many of the secrets that leak in the first place.
- Saviynt centralizes remediation tasks within broader identity governance to drive closure.
Bottom Line on Picking a NHIM Platform
If your top risk is leaked or over-privileged secrets across code, chat, and pipelines, start with a detection and response heavy platform like Entro or Oasis, then backstop with secretless patterns where possible. If your goal is to eliminate secrets in services and CI/CD, pilot Defakto in one or two high-risk pipelines to validate engineering fit. If audit and convergence are pressing, Saviynt brings NHIM into the same controls used for human identities. Breach costs are rising, with the global average at $4.88M in 2024, so shrinking the credential attack surface pays for itself quickly when incidents strike. The NHIM market's importance is also reinforced by large moves like CyberArk's announced acquisition of Venafi, a leader in machine identity, which underlines how central machine identities have become to modern security strategy.
Finally, verify vendor maturity and roadmap fit. Oasis and Defakto are fast-moving entrants with recent funding and recognitions, so expect rapid feature drops and plan a proof of value. Saviynt offers converged governance breadth and transparent marketplace pricing for some modules, which helps budgeting. For user-reported pros and cons, consult independent reviews, for example G2 feedback on Saviynt's learning curve and configuration complexity and G2 feedback on Entro's reporting and RBAC requests.


